Table of Contents
Content Error or Suggest an Edit
Notice a grammatical error or technical inaccuracy? Let us know; we will give you credit!
Investigating the hack
I ran into a WordPress site that was running on a VPS and using a large amount of CPU. Let’s open htop and see what’s going on!
htop
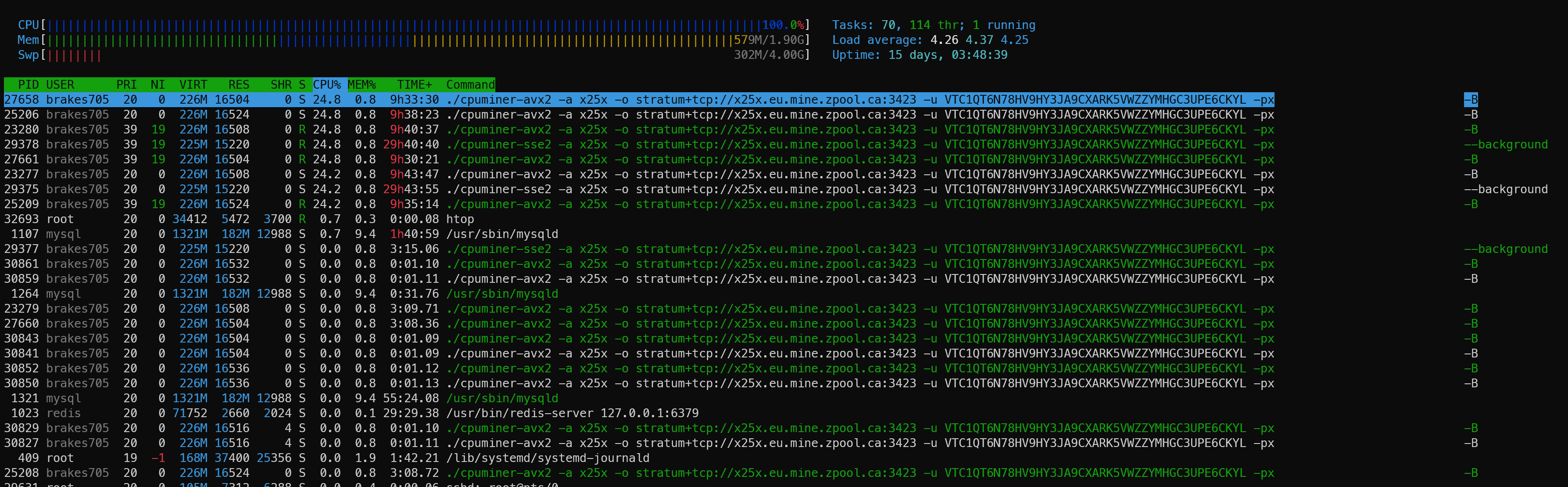
Turns out an account brakes 70599 was running cpuminer-sse2 and cpuminer-avx2 as you can see from the screenshot above.
So let’s see if we can gather some more information!
ps -auxwwwf lsof -p <pid of process >
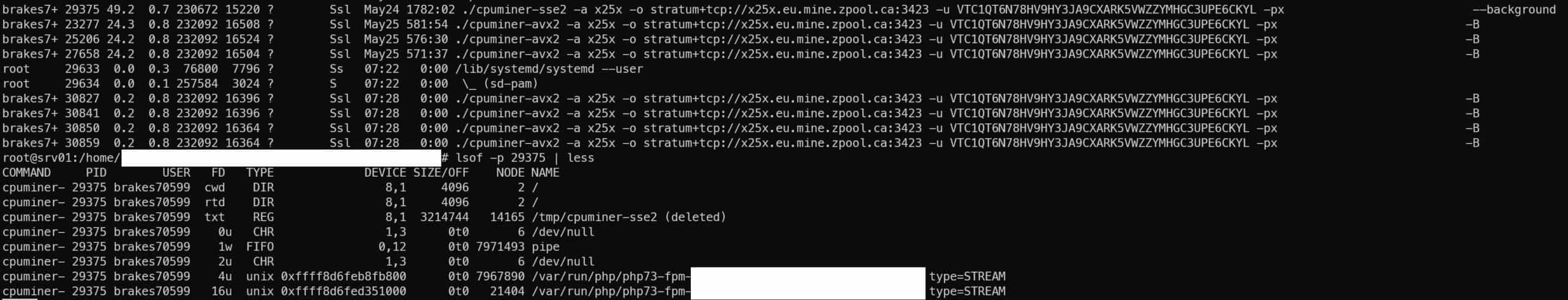
Running lsof provides a list of open files, and as you can see the miner was plopped into /tmp and executed then deleted.
Securing /tmp with noexec
Let’s take a look at /tmp by running the following command.
ls -al /tmp
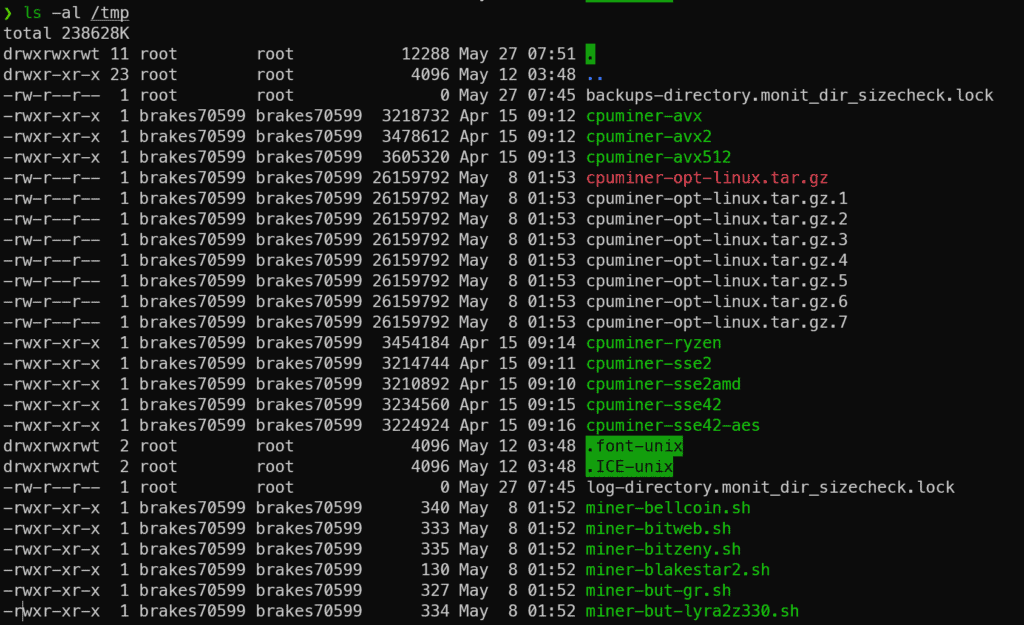
So we can see leftovers from the installation of the cpuminer, as well as binaries and scripts! This server is running on the GridPane platform, and unfortunately, they don’t mount /tmp as non-executable. So let’s protect /tmp so no code can be executed from /tmp
mount -o bind /tmp /tmp mount -o remount,noexec /tmp
If you try and then run a script or program from /tmp it will fail with permission denied. This will however be lost on reboot, so let’s add something to /etc/fstab so this persists upon reboot.
tmpfs /tmp tmpfs defaults,noatime,nosuid,nodev,noexec,mode=1777 0 0
You should now see that /tmp is mounted with noexec!
mount | egrep --color -w '^(tmpfs|/tmp)|/tmp'
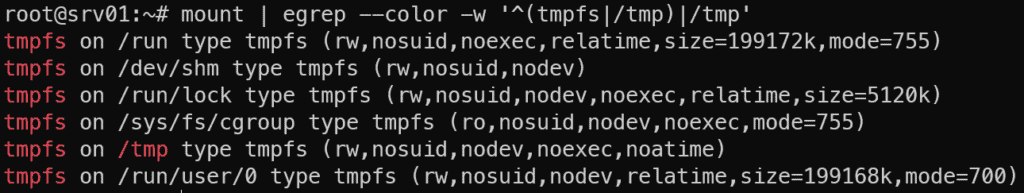
Protecting the /tmp folder from being able to run executable programs from has been something that cPanel has done for years. I’ve submitted a feature request, so please upvote it 🙂
https://roadmap.gridpane.com/b/stack-feature-requests/set-tmp-to-noexec
Further security
What else can we do? There doesn’t look to be a way for the attacker to escalate privileges to root, so for now let’s suspend the account and lock the password.
passwd -l brakes70599
Another issue I have with GridPane is that even though the site is disabled, the system user can’t be disabled. I’ve locked the use as per the command line above, but someone can still sftp into the account with an ssh key if added to the .ssh/authorized_keys file. I submitted a feature request, please upvote.