Last Updated on September 21, 2023 EDT by Jordan
Content Error or Suggest an Edit
Notice a grammatical error or technical inaccuracy? Let us know; we will give you credit!
Attention – Always Test!
Ensure you test your Cloudflare rules after implementation, as they can block some services such as backups, monitoring and management services. Also, make sure to use a VPN to test country blocks.
Other Cloudflare Guides
- Rant, Cloudflare Bot Fight Mode doesn’t provide firewall bypass or whitelist?
- Using Cloudflare Without Changing your Name Servers
- Cloudflare 520 Errors Explained and Investigated
- Secure, Protect and Lock Down your WordPress site with Cloudflare Custom WAF Rules (was Firewall Rules)
- Protecting the WordPress Admin Login with Cloudflare
- Testing and Reviewing Cloudflare Firewall and WAF Rules
- Common WordPress Cloudflare WAF (Web Application Firewall) Rules
Protecting the WordPress Login
Typical WordPress Login Attacks
The WordPress login page is the most popular attack vector for hackers and malware. The brute force login attack is typically what is utilized. In the following article, more innovative attacks target specific usernames after enumerating your users via one of many user enumeration methods.
WordPress Login Attacks Spike Resource Usage
If you have a super secure 32-character password, brute force will be pretty much a useless endeavour for hackers or malware. However, it does cost you resources, each request is considered a dynamic request that will utilize your website’s server resources. Effectively causing a DoS attack if you have a popular site with lots of traffic. This could turn into a DDoS attack and start taking away a good chunk of your server resources, which isn’t good if you run an eCommerce site or are on shared hosting. The server resources should be put towards legitimate visitors and requests.
Hardening WordPress with Additional Security
Cloudflare provides a method to stop automated attacks from hackers or malware. It won’t, however, harden or secure WordPress from targeted attacks or leaking information that could help hackers or malware with a successful compromise of your WordPress site.
It’s always suggested to harden your WordPress instance, this is a topic for another blog post.
Cloudflare WAF Rules for Protecting your WordPress Admin Login
Method #1 – Managed Challenge
The following method will set up what is called a “Managed Challenge” on all links under “/wp-admin” except for “/wp-admin/admin-ajax.php” which is used by some plugins for users browsing the site that are not logged in.
This is my preferred method, as it will block a majority of automated attacks while also allowing yourself and others to gain access to the WordPress admin.
Here is what the rule looks like; you can re-create this rule in your own Cloudflare account.
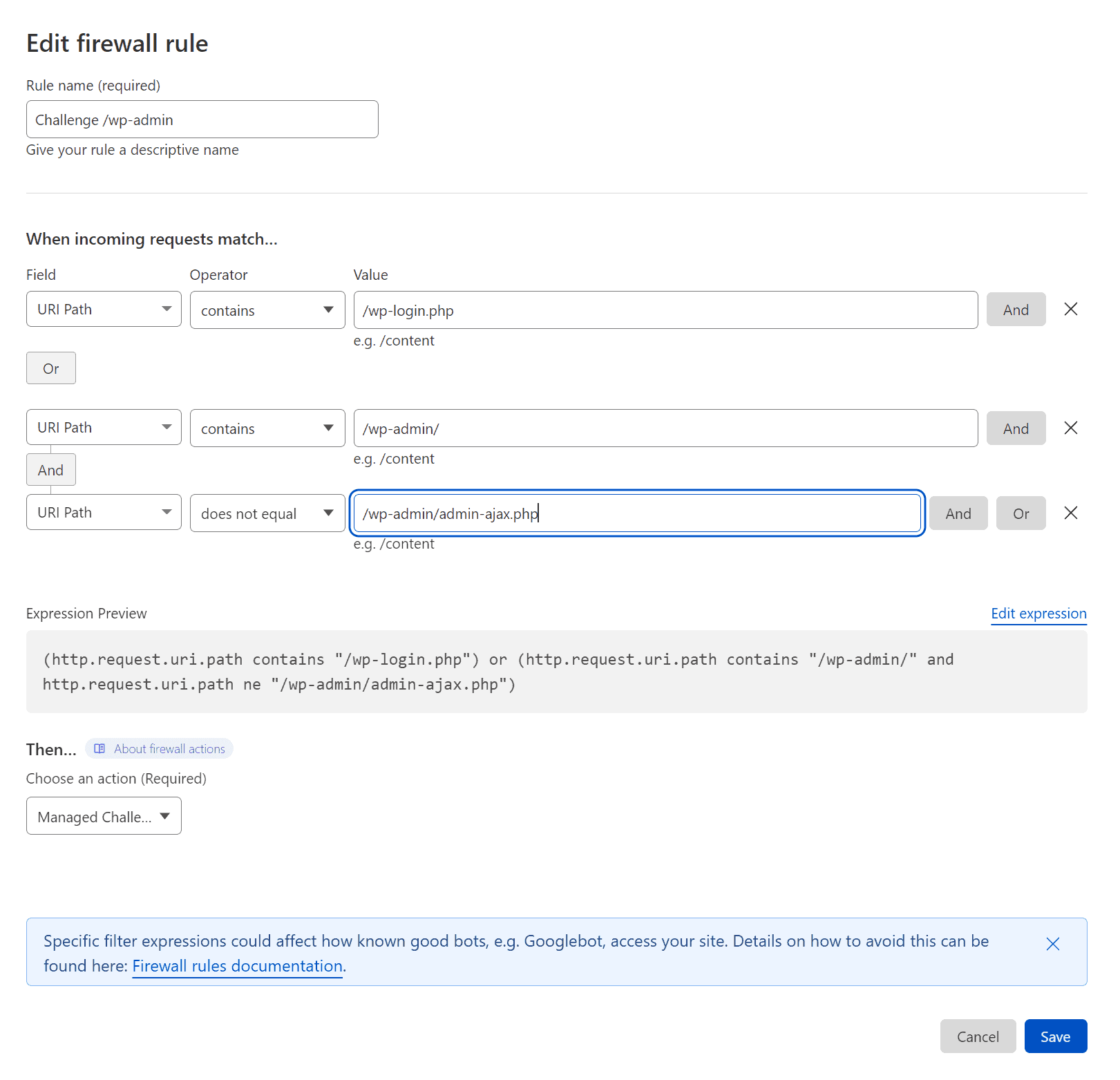
If you want to save some time, you can click on “Edit Expression” and copy and paste the following code.
(http.request.uri.path contains "/wp-login.php") or (http.request.uri.path contains "/wp-admin/" and http.request.uri.path ne "/wp-admin/admin-ajax.php")
Lastly, you want to set “Then..” to “Managed Challenge (Recommended)”
Viola, you’re now blocking login attempts to your /wp-admin with a managed challenge that needs to be solved and will block most automated attacks.
Method #2 – Whitelist IP
You can block all requests to /wp-admin and whitelist your IP address. GridPane has a great article on this.
https://gridpane.com/blog/cloudflare-firewall-rules-for-securing-wordpress-websites/#block-admin
Method #3 – Query String
You can also set a specific query string to the end of your WordPress login URL; GridPane has a great article on this.
https://gridpane.com/blog/cloudflare-firewall-rules-for-securing-wordpress-websites/#block-admin
Testing/Review
Once you have your rules in place, you can test them to ensure they’re effective.
Conclusion
Any method you choose above will work; just ensure you always test!
Last Updated on September 21, 2023 EDT by Jordan