Table of Contents
- Other Cloudflare Guides
- Head to the Juicy Bits. TLDR;
- Introduction
- The Cloudflare WAF
- Managed Cloudflare WAF Rules
- Free vs Pro Cloudflare Managed WAF Rules
- What You Need to Know Before Creating WAF Custom Rules
- (Read First) Important Notes about the Cloudflare WAF Rules In This Guide
- Managing WP’s Cloudflare WAF Rules to Secure Your WordPress Site
- Review and Testing
- Additional Notes
- Additional Resources
- Questions
- 2 – Am I reading this correctly that you do not enable Fail2Ban or the 7G Firewall with GridPane
- Historic Information
- Changelog
Content Error or Suggest an Edit
Notice a grammatical error or technical inaccuracy? Let us know; we will give you credit!
Other Cloudflare Guides
- Rant, Cloudflare Bot Fight Mode doesn’t provide firewall bypass or whitelist?
- Using Cloudflare Without Changing your Name Servers
- Cloudflare 520 Errors Explained and Investigated
- Secure, Protect and Lock Down your WordPress site with Cloudflare Custom WAF Rules (was Firewall Rules)
- Protecting the WordPress Admin Login with Cloudflare
- Testing and Reviewing Cloudflare Firewall and WAF Rules
- Common WordPress Cloudflare WAF (Web Application Firewall) Rules
Head to the Juicy Bits. TLDR;
This is a huge article that covers a lot of topics. If you’re looking for the Cloudflare rules I’ve developed, then click on the button below 🙂
Attention – Always Test!
Ensure you test your Cloudflare rules after implementation, as they can block some services such as backups, monitoring and management services. Also, make sure to use a VPN to test country blocks.
Introduction
This guide was born from my experience helping someone in the GridPane private Community Forums with a similar issue. By providing them with the rules I had used to secure another site, I was able to help them lock down their own site successfully. In this article, we’ll share those same rules so you can protect your website with Cloudflare’s WAF rules.
This guide will use Cloudflare’s WAF rules to secure your website. Whether you’re on the Cloudflare Free Plan or the Pro Plan, we’ll show you how to make the most of your available rules. Following our step-by-step instructions, you can block common WordPress attacks.
It’s important to note that attacks on your WordPress site compromise its security but can also cause significant resource wastage on your server. Every time your WordPress site receives an un-cached request, PHP is triggered, generating a response. If there are enough automated malicious requests, your server’s resources may spike, slowing down your site and other sites hosted on the same server. By implementing Cloudflare’s WAF rules, you can prevent these attacks and ensure your server’s resources are used effectively. Reducing the risk of downtime due to overloaded server resources and helping your site quickly respond to legitimate requests.
The Cloudflare WAF
Cloudflare’s Web Application Firewall (WAF) is a powerful tool for analyzing and filtering traffic destined to your WordPress site. The Cloudflare WAF analyzes incoming traffic and blocks requests that match predefined rules or patterns. This helps to prevent attacks before they can even reach your server, reducing the risk of data breaches, malware infections, and other security incidents. Most importantly, wasted resources handling malicious requests from automated attacks.
To set up Cloudflare WAF, you’ll need to configure a series of rules that tell the firewall how to handle different types of traffic. These rules can be as simple or complex as you need them to be, and Cloudflare provides a range of prebuilt rules that you can use as a starting point. Once your rules are in place, the WAF will begin monitoring your traffic and blocking any requests that violate your security policies. Overall, Cloudflare WAF is a powerful and effective tool for securing your website against common web application attacks, and it’s a must-have for anyone looking to protect their online assets from malicious actors.
Cloudflare Custom WAF Rules
The new Firewall Rules UI provides a more streamlined and user-friendly experience for creating and managing Firewall Rules. It includes new features such as improved rule management, custom rule groups, and the ability to set multiple actions per rule. Additionally, the new UI is integrated with Cloudflare’s Managed Rules, making enabling and managing Managed Rules for your website easier.
The main differences between Firewall Rules and WAF custom rules are as follows:
- Improved response for Block action: The Block action in WAF custom rules provides a more detailed response than in Firewall Rules, allowing you to understand better why a request was blocked.
- New Skip action: WAF custom rules include a new Skip action that replaces both the Allow and Bypass actions in Firewall Rules. This provides a more flexible way to handle certain types of traffic.
- Custom rules are evaluated in order: Unlike Firewall Rules, custom rules are evaluated in the order they are defined. This allows you to define more complex rules that consider multiple factors.
- Logs and events: WAF custom rules provide more detailed logging and events than Firewall Rules, allowing you to better track and analyze traffic to your website.
- New API and Terraform resources: WAF custom rules include a new API and Terraform resources, making it easier to automate creating and managing custom rules.
New Skip Action Screenshots
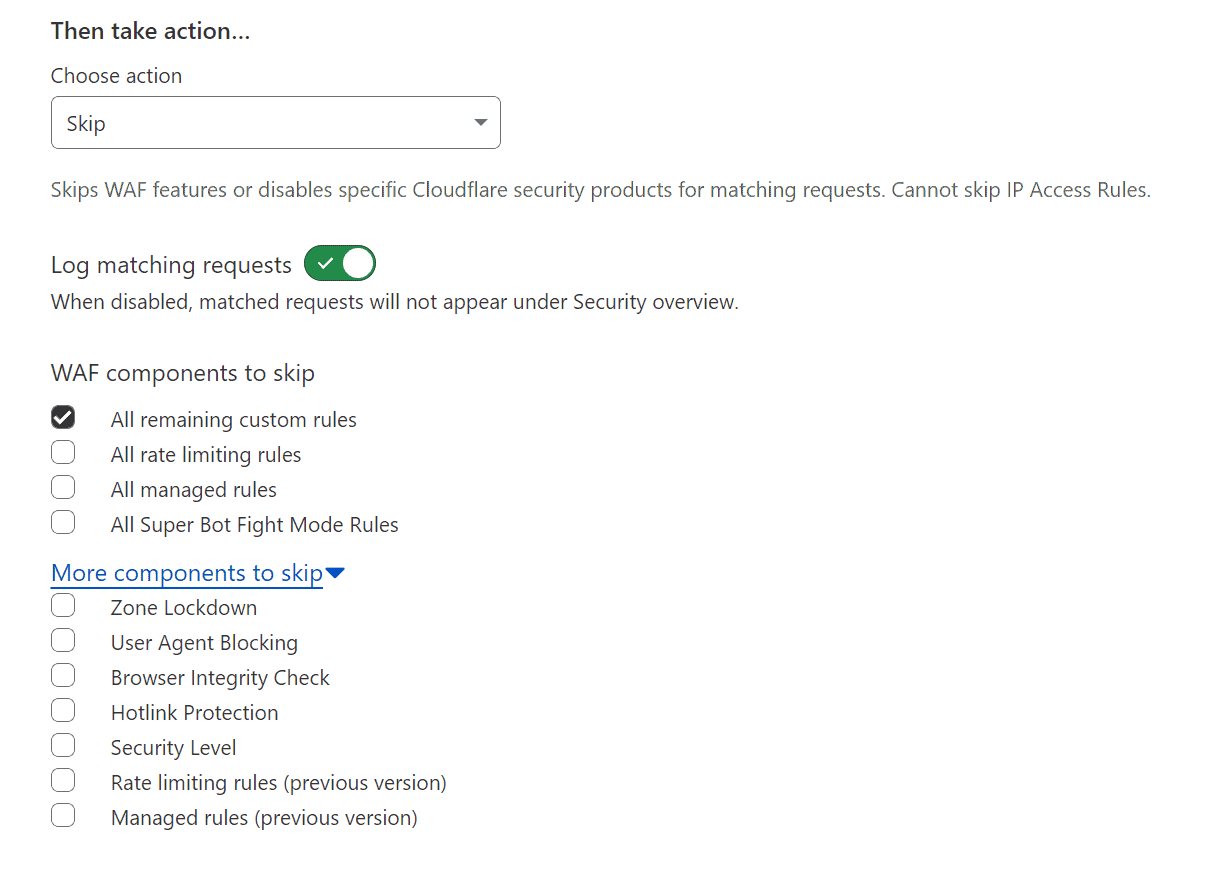
Cloudflare WAF Custom Rules Order Evaluation
With custom rules, the order of the rules determines which action is executed. If two custom rules match an incoming request, the action in the first rule will be executed, and the evaluation of other rules will stop. For instance, if the first custom rule has a Block action and the second rule has a Skip action, the request will be blocked, as the Block action stops evaluating the remaining rules.
Cloudflare says it best.
Firewall rules actions have a specific order of precedence when using priority ordering. In contrast, custom rules actions do not have such an order. Custom rules are always evaluated in order, and some actions like Block will stop the evaluation of other rules.
For example, if you were using priority ordering and had the following firewall rules with the same priority both matching an incoming request:
Firewall rule #1 — Priority: 2 / Action: Block
Firewall rule #2 — Priority: 2 / Action: Allow
The request would be allowed, since the Allow action in Firewall Rules takes precedence over the Block action.
In contrast, if you create two custom rules where both rules match an incoming request:
Custom rule #1 — Action: Block
Custom rule #2 — Action: Skip (configured to skip all remaining custom rules)
The request would be blocked, since custom rules are evaluated in order and the Block action will stop the evaluation of other rules.
https://developers.cloudflare.com/waf/reference/migration-guides/firewall-rules-to-custom-rules/#custom-rules-are-evaluated-in-order
Managed Cloudflare WAF Rules
Managed rules are pre-built sets of WAF rules from Cloudflare designed to protect against common attacks, such as SQL injection, cross-site scripting, and more. Cloudflare manages and updates these rules, meaning you don’t need to worry about configuring them yourself. Instead, you can enable the rules you need and let Cloudflare handle the rest.
Managed rules are available in various categories, including OWASP Top 10, WordPress, Drupal, and more. Each category contains a set of rules tailored to the specific needs of the platform or application, helping to ensure that your site is protected against the latest threats. Additionally, Cloudflare periodically updates these rules to ensure they remain effective against new and emerging attack vectors.
Free vs Pro Cloudflare Managed WAF Rules
Under the Free plan, users can access a limited set of Cloudflare Managed WAF Rules, which are pre-built rule sets designed to protect against specific types of attacks. The Free plan includes up to five Cloudflare Managed WAF Rules, while the Pro plan includes up to 20.
Cloudflare announced on 03/15/2022 that there would be a Free Managed WAF Ruleset for all Cloudflare Customers.
One of the most significant benefits of the Pro plan is access to frequent rule updates. Cloudflare regularly updates its Managed WAF Rules to help protect against the latest threats, and Pro plan users get priority access to these updates.

Cloudflare Pro Managed Rules Previous Version Screenshots
Here are some screenshots of the Cloudflare Managed Rules under a Pro Account



Cloudflare Pro Managed Rules New Version Screenshots

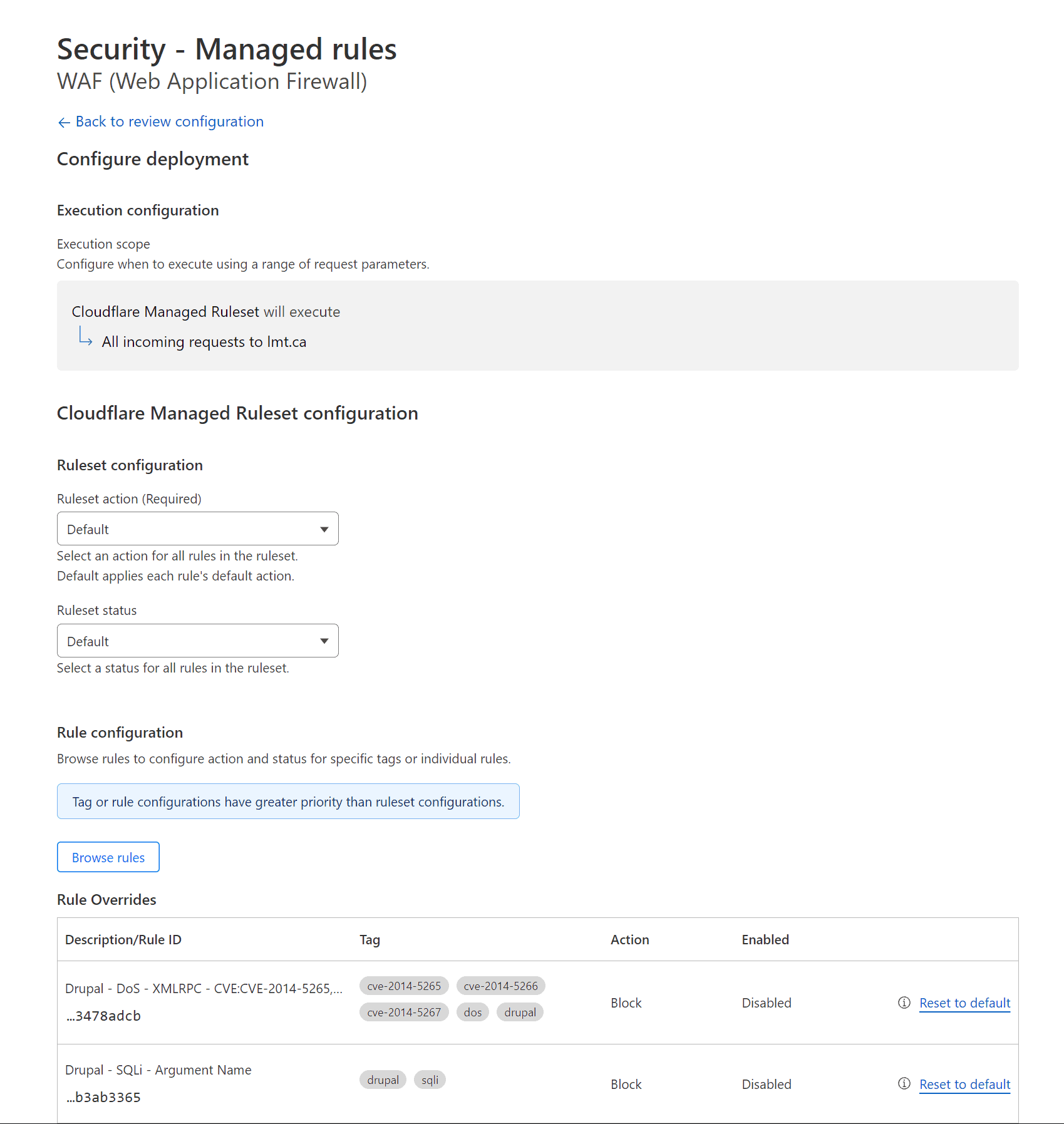

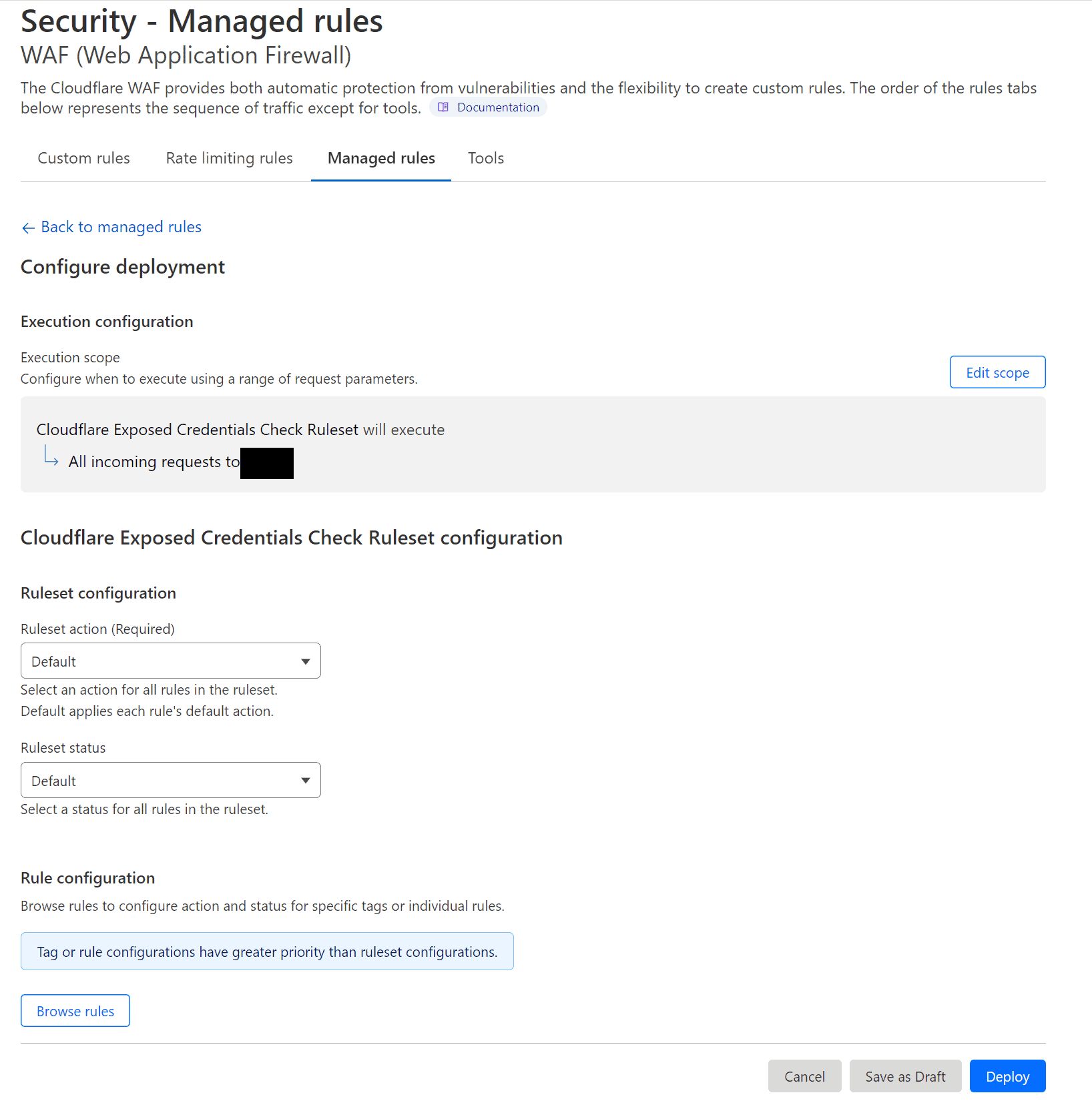
What You Need to Know Before Creating WAF Custom Rules
Here are some important points you must consider when creating WAF Custom Rules; ensure that you consider them before proceeding.
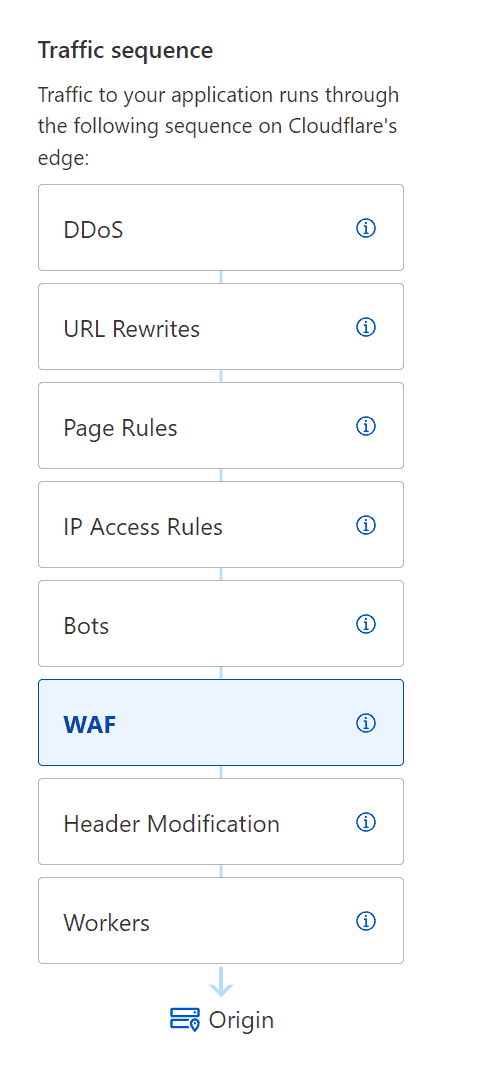
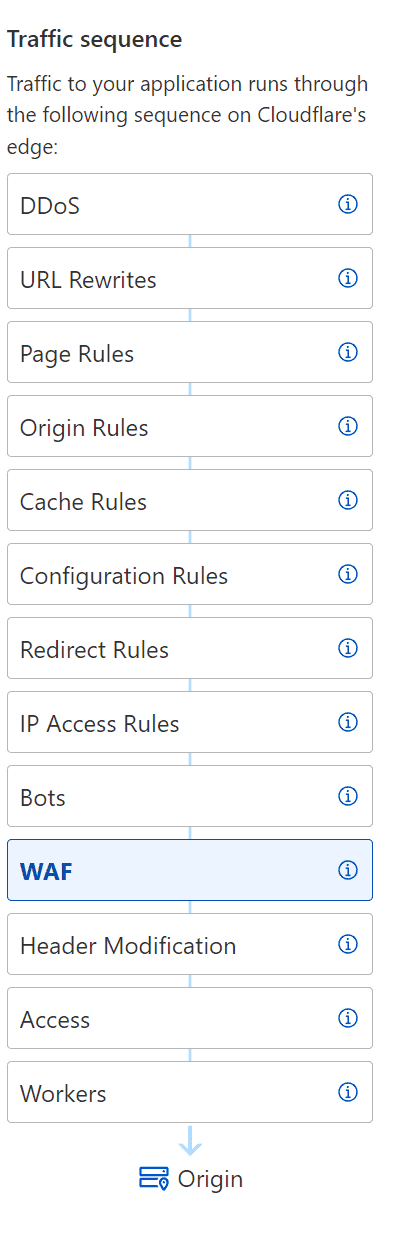
Traffic Sequence
Understanding how traffic flows through Cloudflare servers on the edge is crucial for troubleshooting. While Cloudflare provides a helpful diagram to visualize this flow, it’s unfortunately not always easy to find. The diagram typically appears to the left of each service you’re using, serving as a reminder of when your service is engaged on the edge.
The traffic sequence diagram illustrates how your website’s traffic flows through Cloudflare’s servers on the edge. This includes the steps of a request, such as DNS resolution, SSL negotiation, caching, and more. By understanding this flow, you can identify potential issues when troubleshooting.
IP Access Rules (Deprecated)
Always check your access rules under your account, as with IP Lists; they can be domain or account-specific. So any domains you have access to due to being a member of the account will not utilize account-specific rules.
Update
Cloudflare has changed how IP Access Rules work as per https://developers.cloudflare.com/waf/tools/ip-access-rules/ they recommend using a custom firewall rule instead.
Recommendation: Use custom rules instead
Cloudflare recommends that you create custom rules instead of IP Access rules to perform IP-based or geography-based blocking (geoblocking):
For IP-based blocking, use an IP list in the custom rule expression.
For geoblocking, use fields such as AS Num, Country, and Continent in the custom rule expression.

Adding Cloudflare Rules using Expression Builder
This guide’ll show you how to add Cloudflare rules using the expression builder. This powerful tool allows you to create complex rules to protect your website against various threats, including SQL injection, cross-site scripting, etc. Following our step-by-step instructions, you can easily configure the expression builder and create rules tailored to your needs. Below is a animated gif showing how this is done.
Cloudflare WAF Challenge Types
Cloudflare protects websites by challenging visitor traffic in several different situations, including:
- When a visitor’s IP address has shown suspicious behavior online, as tracked by Project Honeypot.
- When the website owner has blocked the country associated with the visitor’s IP address.
- When the visitor’s actions have triggered a firewall rule enabled by the website owner.
If a visitor passes the challenge, their request is allowed to proceed. However, if they fail the challenge, their request will be blocked to protect the website against potential threats.
Managed Challenge (Automated Challenge)
Managed challenges, Cloudflare selects the appropriate type of challenge based on the characteristics of a request, reducing the need for CAPTCHAs and minimizing the impact on human users. Depending on the characteristics of a request, Cloudflare may choose to present a non-interactive challenge page, a custom interactive challenge (such as clicking a button), or Private Access Tokens (using recent Apple operating systems), among other options.
JS Challenge
JS challenges are presented to visitors as a challenge page that requires no interaction, but instead relies on JavaScript processing by the visitor’s browser. The visitor will need to wait until their browser finishes processing the JavaScript, which typically takes less than five seconds
Interactive Challenge (Force User Action)
On the other hand, interactive challenges require visitors to actively engage with the challenge page by solving an interactive challenge. However, Cloudflare does not recommend using interactive challenges, as they can impact legitimate traffic and reduce the usability of your website.
You can read more about Cloudflare challenges at https://developers.cloudflare.com/fundamentals/get-started/concepts/cloudflare-challenges/
(Read First) Important Notes about the Cloudflare WAF Rules In This Guide
PLEASE READ THE FOLLOWING ITEMS BEFORE PROCEEDING!
This guide is updated regularly, so check back frequently and reference the changelog at the bottom.
Here’s a screenshot of the typical rules you will create in the Cloudflare WAF; these rules below achieve the following.
- Allow and Block specific URL Queries, URLs, and User Agents while allowing customization.
- Protect /wp-admin with a Managed Challenge.
- Allow Good Bots and User Agent, URI Query Strings (Common bots and services added)
- All traffic outside Canada will have a forced JS Challenge.
Cloudflare Previous Cloudflare Firewall Rules Screenshot
This is what the rules would have looked like before Cloudflare was renamed and changed from Cloudflare Firewall to Cloudflare WAF.
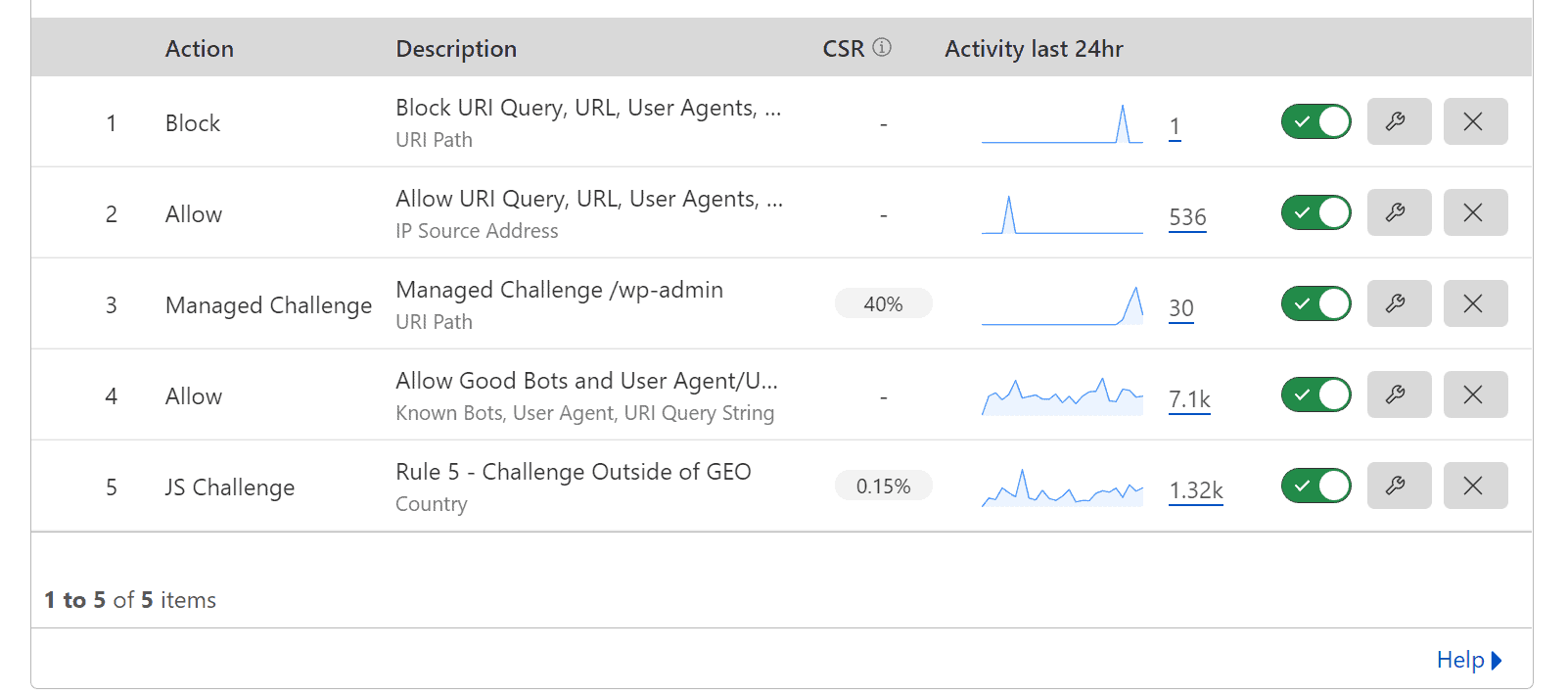
Cloudflare WAF Custom Rules Screenshot
Here is what the new Cloudflare WAF rules will look like going forward.
Multiple Expressions with “and/or” in Expression Builder
It’s important to be cautious when using multiple “and/or” expressions in a rule, as these may not always work correctly. When creating a rule involving multiple expressions, it’s essential to test it thoroughly to ensure it functions as expected. In some cases, creating separate rules for different conditions may be a more effective approach.
For example, if you’re trying to apply a rule that challenges traffic outside Canada, incorporating “and/or” expressions may break the rule. Instead, creating a separate rule for the Challenge outside of Canada may be more effective. By separating the conditions into individual rules, you can avoid potential conflicts and ensure your website’s security is not compromised.
The following are the Cloudflare WAF rules that we use in production! Enjoy!
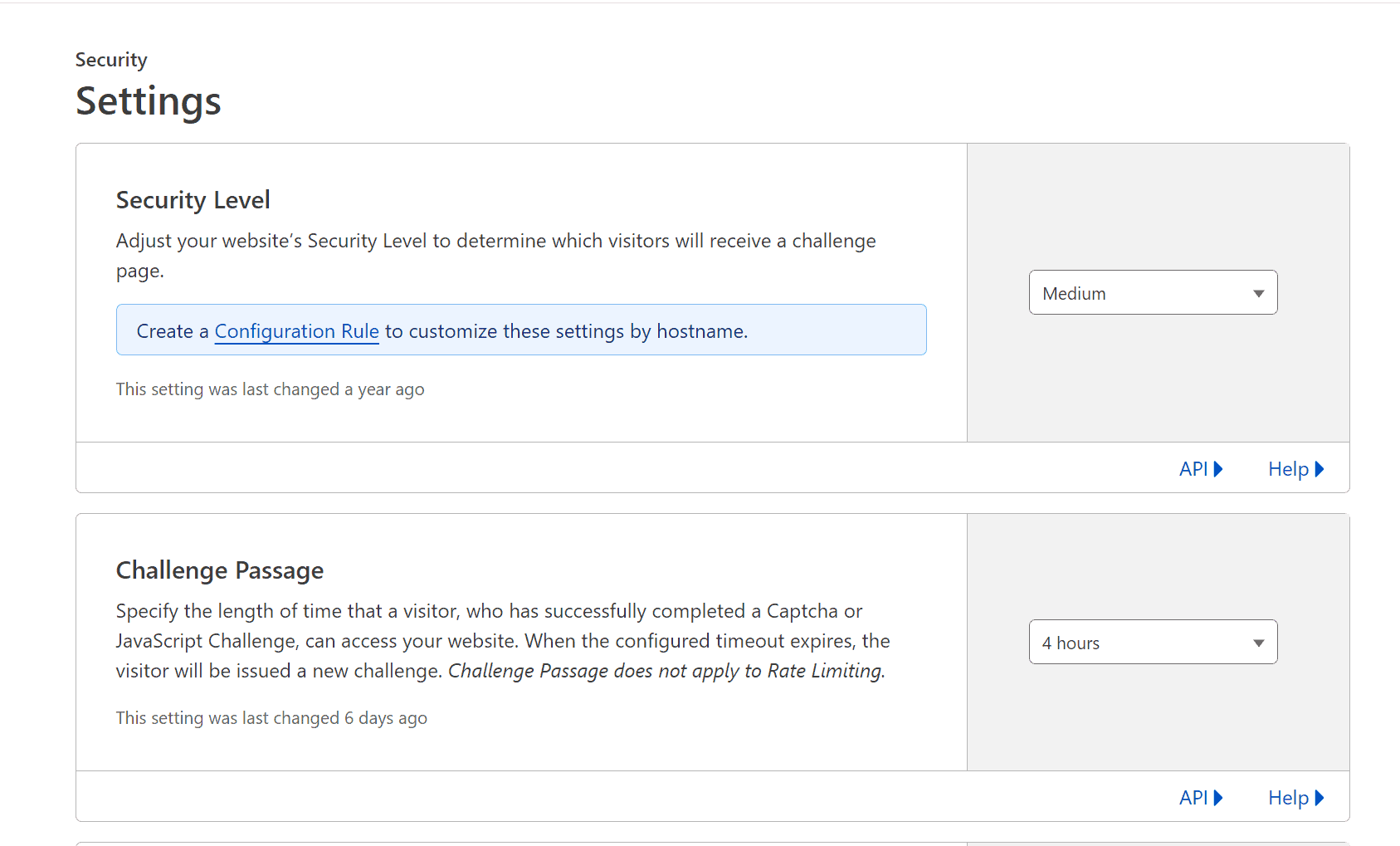
Managed Challenge – Challenge Passage Setting (Timeout)
Attention
The following notes are essential if you’re having issues with your site when editing from the backend.
The rules below include the Cloudflare “Managed Challenge” feature, which will challenge visitors with a captcha or JavaScript challenge when they visit your site. You might run into issues if you use the Managed Challenge action to block the WordPress admin login.
You will be issued a new challenge if logged into your WordPress site and working away in the admin dashboard for more than the Challenge Password time. This might cause issues in the WordPress editor, specifically when saving a page or post. This is due to the Cloudflare Managed Challenge kicking in for all requests, causing the request to save a page or post to fail.
To correct this, you can open a new window, visit the WordPress admin login, solve the Managed Challenge and then go back and trigger a save within the WordPress editor. A better solution is to set the Challenge Passage to longer, such as 4 hours.
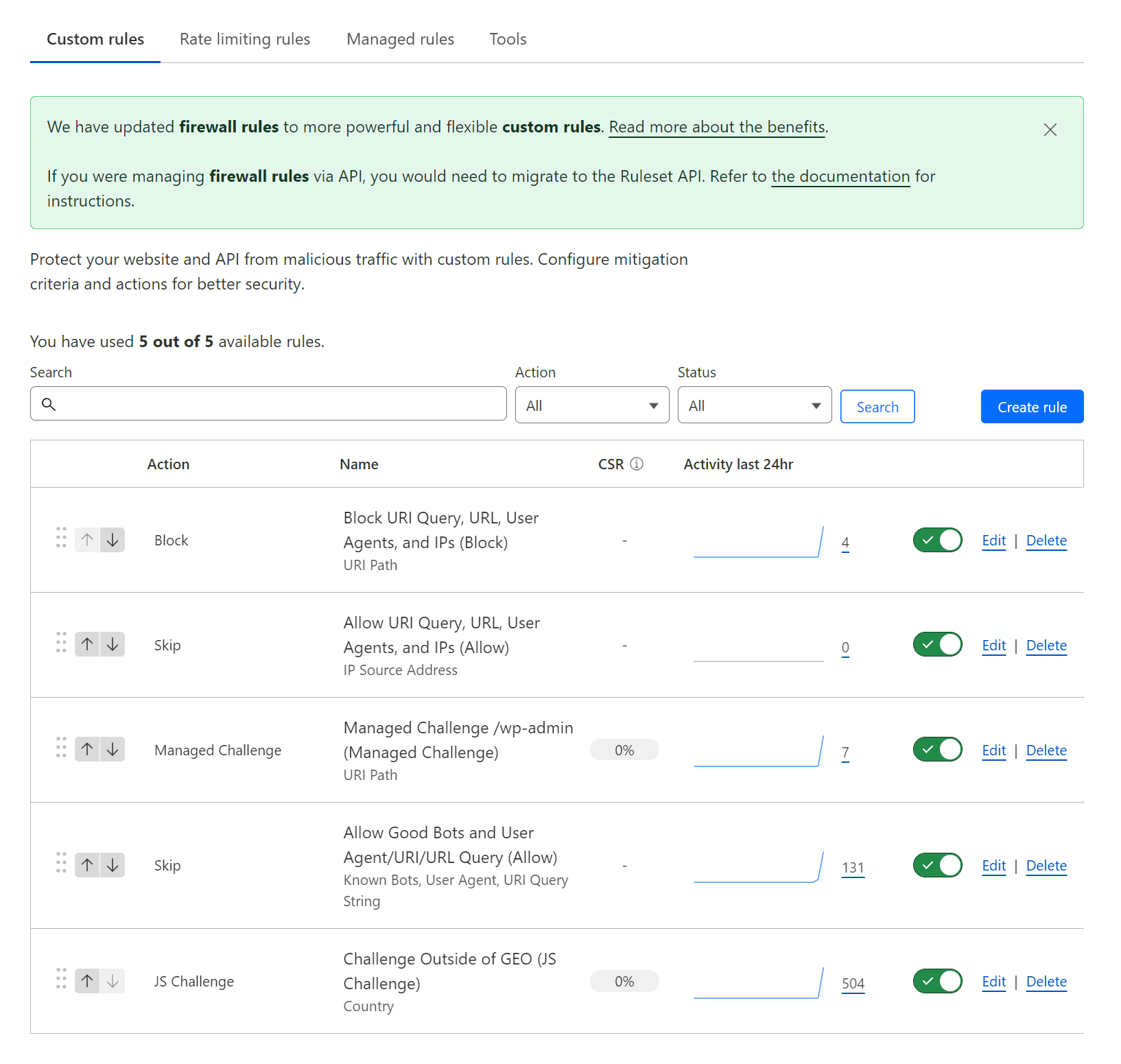
Managing WP’s Cloudflare WAF Rules to Secure Your WordPress Site
Download Rules on GitHub
You can access all the mentioned rules below in a single-page GitHub markdown document if you want to implement these rules. Please note these may be updated more frequently than this page.
Rule Logic
The logic behind these rules is an easy-to-understand flow, as Cloudflares WAF works by matching and then you can control that match with either a block, skip, managed challenge, interactive challenge or js challenge.
You always want to have your skip rules first, then your block rules. This will ensure that anything you wish to have skip the Cloudflare WAF doesn't get caught in a block rule.
- R1V2 - Block URI Query, URL, User Agents, and IPs (Block)
- R2V2 - Allow URI Query, URL, User Agents, and IPs (Allow)
- R3V2 – Managed Challenge /wp-admin (Managed Challenge)
- R4V2 – Challenge Outside of GEO (JS Challenge)
R1V2 - Block URI Query, URL, User Agents, and IPs (Block)
Use this rule for all your blocking rules, URI Queries, URLs, User Agents and IPs. I don't have much here, except for /xmlrpc.php because we all know why. I also found that the wp-activity-log plugin was leaving non-mirrored log dad in the uploads folder unprotected.
Action: Block
(http.request.uri.path eq "/wp-content/uploads/wp-activity-log/non_mirrored_logs.json") or (http.request.uri.path eq "/xmlrpc.php")
R2V2 - Allow URI Query, URL, User Agents, and IPs (Allow)
Advice / Tip
For the most part, I've been using User-Agent's here instead of IP's. Granted, hackers could bypass this by faking their user agents. We're more concerned about automated attacks at this point, and until hackers start manufacturing User Agents, it's not a concern.
This rule will allow known Cloudflare good bots; some might not be good bots to you. Double-check their list at https://radar.cloudflare.com/verified-bots
I have also added some custom detection via User-Agent and URI Query. Some might think this isn't secure, and IP is the only 100% secure method. If something uses the User-Agent Better Uptime, it's a targeted attack, not automated, and there's a more significant issue.
- Shipstation
- Metorik
- Wordfence Central
- Better Uptime
Feel free to add any services you wish here.
Action: Skip
- All remaining custom rules
- All rate-limiting rules
- All managed rules
- All Super Bot Fight Mode Rules
(ip.src in {88.99.145.111 88.99.145.112 195.201.197.31 136.243.130.174 144.76.236.242 136.243.130.52 116.202.131.150 116.202.233.15 116.202.193.3 168.119.2.157 49.12.124.233 88.99.146.248 139.180.140.55 104.248.114.9 192.81.221.63 45.63.10.187 45.76.137.73 45.76.183.23 159.223.99.132 198.211.127.63 45.76.126.238 159.223.105.100 161.35.121.79 208.68.38.165 147.182.131.77 174.138.35.170 149.28.228.237 45.77.106.232 140.82.15.60 108.61.142.158 45.77.220.240 67.205.160.142 137.184.156.126 157.245.142.130 159.223.127.73 198.211.127.43 198.211.123.140 82.196.0.67 188.166.158.7 46.101.79.124 192.248.168.22 78.141.225.57 95.179.214.63 104.238.190.161 95.179.208.185 95.179.220.182 66.135.5.151 45.32.7.254 149.28.227.238 8.9.37.67 149.28.231.28 142.132.211.19 142.132.211.18 142.132.211.17 159.223.166.150 167.172.146.73 143.198.184.39 161.35.123.156 147.182.139.65 198.211.125.219 185.14.187.177 192.81.222.35 209.97.131.196 209.97.135.165 104.238.170.64 78.141.244.3 217.69.0.229 45.63.115.86 108.61.123.152 45.32.144.195 140.82.12.121 45.77.99.218 45.63.11.48 149.28.45.216 209.222.10.118 147.182.130.252 149.28.62.18 207.246.127.103 157.245.137.38 207.246.120.94 157.245.128.151 45.77.148.172 142.93.11.155 144.202.2.38 104.248.238.131 45.77.148.172 141.95.192.2 176.9.40.54 176.9.106.100 176.9.21.94})
or (http.request.uri.query contains "bvVersion")
or (http.request.uri.query contains "wc-api=wc_shipstation")
or (http.user_agent contains "Zapier")
or (http.user_agent contains "Metorik API Client")
or (http.user_agent contains "Wordfence Central API")
or (http.user_agent eq "Better Uptime Bot")
or (http.user_agent eq "ShortPixel")
or (http.user_agent contains "umbrella bot")
or (http.user_agent contains "Integrately")
or (http.user_agent contains "Uptime-Kuma")
or (cf.client.bot)
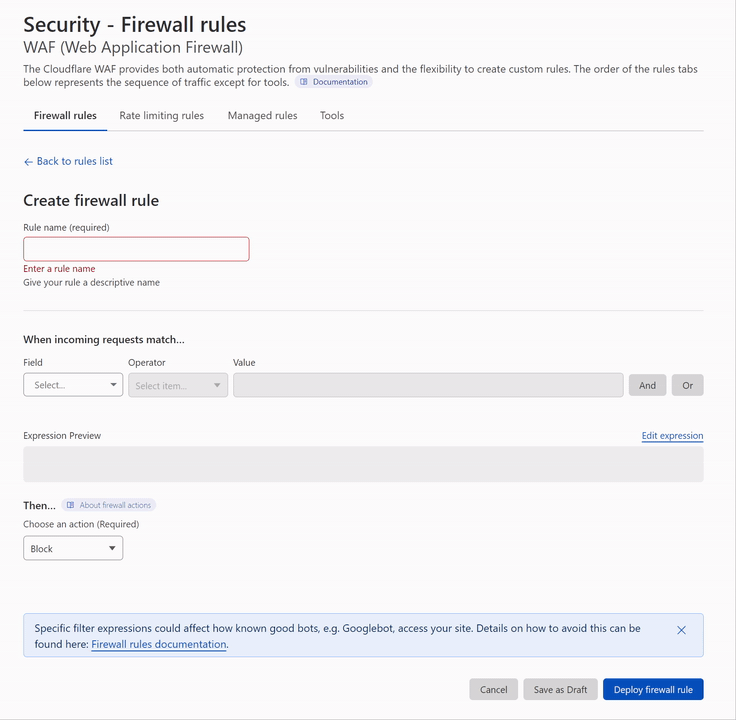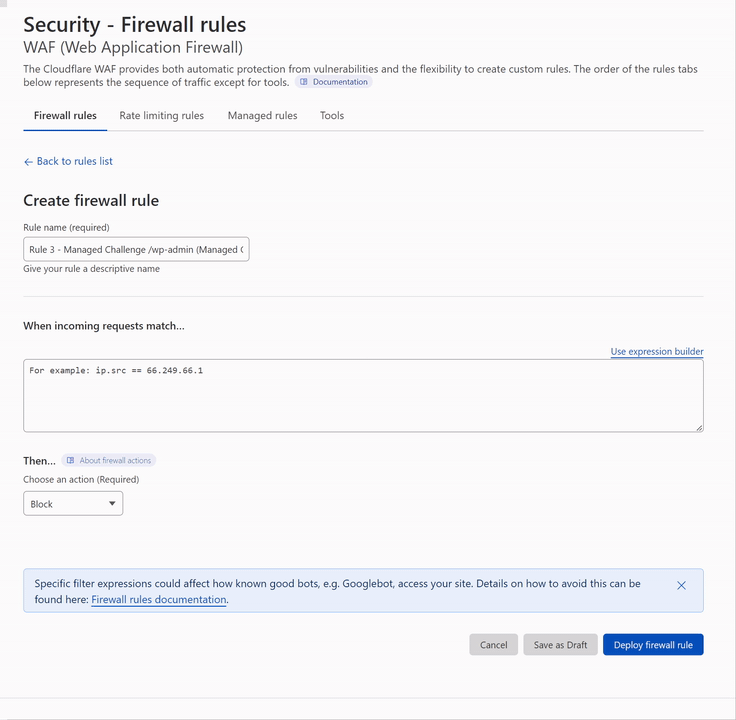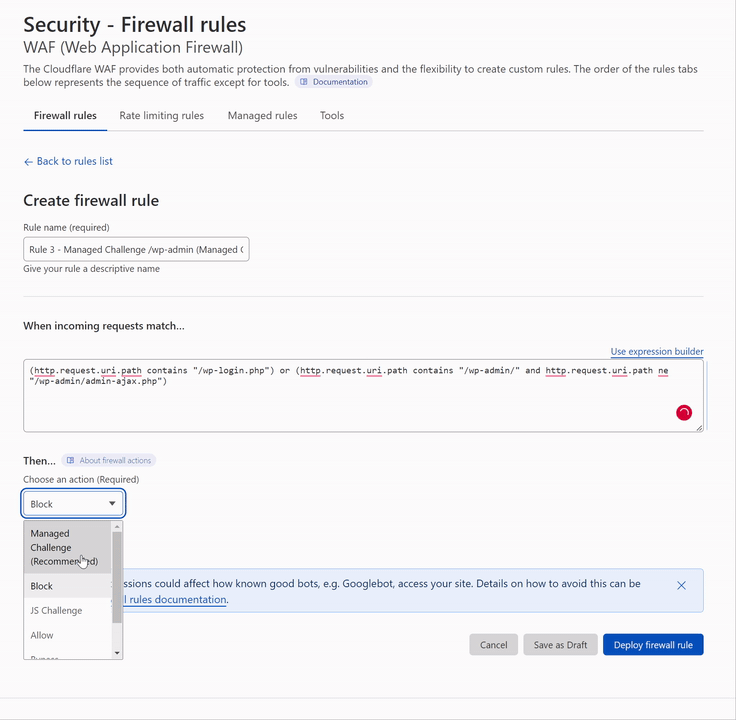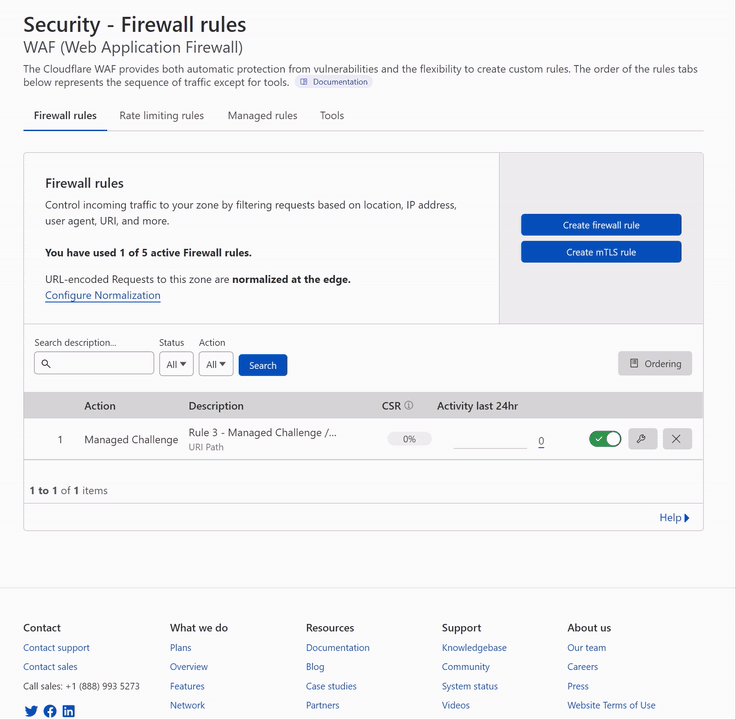
R3V2 – Managed Challenge /wp-admin (Managed Challenge)
Update
I've updated this rule to bypass "/wp-admin/js/password-strength-meter.min.js" as this is used for the WooCommerce register section on the "My Account" page when not logged in and allowing new registrations to set passwords.
Self-explanatory requires a managed challenge to access /wp-admin but allows /wp-admin/admin-ajax.php due to plugins triggering on the front end for non-logged-in users.
It's been asked why Managed Challenge, and for the most part, this is totally up to you; you can use whatever you like. This should really be set to Interactive Challenge if you want to force a captcha and be even more strict.
Action: Managed Challenge
(http.request.uri.path contains "/wp-login.php") or (http.request.uri.path contains "/wp-admin/" and http.request.uri.path ne "/wp-admin/admin-ajax.php" and not http.request.uri.path contains "/wp-admin/js/password-strength-meter.min.js")
R4V2 – Challenge Outside of GEO (JS Challenge)
This rule is optional, but you can require all traffic outside of your known target geographical market to pass a challenge. This is set to JS Challenge as you want to make sure the visitor is using a browser that can process Javascript. Managed Challenge could also work.
Action: Managed Challenge
(ip.geoip.country ne "CA")
Review and Testing
Basic Testing
As always, review and test your Cloudflare Firewall/WAF rules. Here's a guide that talks about this specific subject.
Using Firewalker (Advanced)
I stumbled upon this project called firewalker, which uses the wirewalker Cloudflare rule engine
Firewalker builds on top of Cloudflare's wirefilter rule engine and provides API to construct the requests in JS. After all, if the tests for your workers are in JS, why not to use the same syntax for the WAF rules?
https://github.com/SerCeMan/firewalker
I'm not a pro at nodejs, typescript or even yarn. So it took me a while to figure this out. But here's the breakdown.
- Use a linux instance, WSL or macOS with nodejs 12, it doesn't work with 14 or 16. Check out nvm, it's really cool way of switching nodejs versions.
- Clone the repository somewhere
git clone https://github.com/SerCeMan/firewalker.git
- Use yarn to install required packages, you should have no errors ;)
cd firewalker yarn install
- Run "yarn test" and you should get a bunch of success messages. This is because it's running against the test/firewall.tests.ts file
- Delete the test/firewall.tests.ts file and use the following simple short test file. You can copy and paste the Cloudflare expression code
import {Firewall, Request} from '../src';
import {URLSearchParams} from 'url';
describe('Standard fields', () => {
let firewall: Firewall;
beforeEach(() => {
firewall = new Firewall();
});
it('Testing Original Rule', () => {
# Cloudflare expression to test.
const rule = firewall.createRule(`
(http.request.uri.path contains "/wp-login.php")
or (http.request.uri.path contains "/wp-admin/" and http.request.uri.path ne "/wp-admin/admin-ajax.php")
`);
# Tests to run on the expression.
expect(rule.match(new Request('http://example.org/wp-admin/'))).toBeTruthy();
expect(rule.match(new Request('http://example.org/wp-admin/admin-ajax.php'))).toBeFalsy();
expect(rule.match(new Request('http://example.org/wp-admin/wp-login.php'))).toBeTruthy();
expect(rule.match(new Request('http://example.org/wp-admin/wp-admin/js/password-strength-meter.min.js'))).toBeFalsy();
});
it('Testing New Rule 3', () => {
const rule = firewall.createRule(`
(http.request.uri.path contains "/wp-login.php") or (http.request.uri.path contains "/wp-admin/" and not http.request.uri.path in {"/wp-admin/admin-ajax.php" "/wp-admin/js/password-strength-meter.min.js"})
`);
expect(rule.match(new Request('http://example.org/wp-admin/'))).toBeTruthy();
expect(rule.match(new Request('http://example.org/wp-admin/admin-ajax.php'))).toBeFalsy();
expect(rule.match(new Request('http://example.org/wp-admin/wp-login.php'))).toBeTruthy();
expect(rule.match(new Request('http://example.org/wp-admin/wp-admin/js/password-strength-meter.min.js'))).toBeFalsy();
});
});
- Run "yar test"
Additional Notes
Automating Rule Setup for Multiple Domains
This is something that can be scripted via the API. I will hopefully be releasing a script to do this :) I have released the script and it's not 100% but it works, I will be improving it as I see fit. It's within the same Github repository as the rules, and the file name is cloudflare-wordpress-rules.s
Terraform
I haven't played with this yet, but will be implementing it within my own workflow!
Google Crawl Errors
If you have issues with Google crawling your site, check this troubleshooting crawl errors page from Cloudflare.
https://support.cloudflare.com/hc/en-us/articles/200169806-Troubleshooting-crawl-errors
Additional Resources
The following is additional Cloudflare firewall rules specific to WordPress that you can also use and combine with the rules above.



Questions
1 - Using Cloudflare and GridPane
We have a client who has a woocomerce site with logins and is gettting a lot of attention from unwanted traffic, I currently am using cloudflare & F2Ban (F2Ban sending IP Data to Cloudflare) as well as Gridpaine 7 Waf. Client is not happy with the user experience, real clients and at times getting Bland your banned messages, as well as the amount of complaints from users has got client worried security is to strict and turning away clients. They have also now come back with some very specific requests on how they would like the user experience to be, Eg. showing how many attempts left to try, 2FA for admin users, access to a reset password button.
Trying to work out the best way forward for all of this.
The best solution I have come up with is still using Cloudflare but upping from standard security by adding rules IE discovered this from you. Managing WP - All about Managing WordPress – 10 Aug 22This article stems from assisting someone in the GridPane private Community Forums to lock their site to allow only specific countries and prompt a managed and then using Wordfence for firewall and 2FA along with https://www.limitloginattempts.com/ to give the user experience the Client has requested. (In description this plugin says it works with Wordfence)
Keen to hear your thoughts and the settings you whould use.
do you have a list of what settings you use in wordfence?
do you use the paid wordfence?
what settings do you use in Gridpane security when using Wordfence, 7waf off?(as dont want multiple Waf's) do you use any "additional measures" in Gridpane dash? I see Wordfence looks like it also addresses some of these.
If you decide to go with Cloudflare, turn off all GridPane security for the most part. You will want to keep some options enabled that Cloudflare wouldn't provide, anything that does on-host protection. So, under the "Additional Measures," this would be what I'm speaking to. Any security measures you implement should always be performant, so GridPane additional security will always be performant as it's implemented using the web server and not a PHP plugin, which is less performant.
The rules I provided in that article are pretty much all you need; the rules follow this ideology.
- Block all automated attacks to /wp-admin with a managed challenge, but allow /admin-ajax.php.
- Put in a geo-location managed challenge if you service only specific markets. For instance, if 100% of your customer base is in Nort America, then allow Canada and USA through and JS Challenge for the rest.
- Allow good bots based on Cloudflare's good bot rules.
- Allow specific services that you require to access your site, ahrefs, betteruptime and etc.
Automated attacks can be headless, which is a script and usually can't bypass the js and managed challenges. There is other software that you can run on a desktop/laptop computer that can bypass js and captcha challenges; the software will show the challenge, and the user has to solve it, and then the software can begin it's attack. You'll find these are more often used for card testing, and less for brute-force attacks.
You could also look at using Cloudflare Access to restrict access to WordPress admin backend; it's a double authentication but would help even further.

You could still enable fail2ban here with GridPane if someone is targeting you specifically to brute force your admin login or the Limit Login Attempts plugin.
I really only use WordFence for its live patching firewall; if a plugin does have a security issue that can be actively exploited WordFence will live patch and the attack will fail. But it won't protect the site if WordFence doesn't know about the security issue. So just be aware of that, there's lots of ways a plugin with a security issue can make it onto a site, clients uploading plugins, a plugin that hasn't been updated due to a license expiring and etc.
I don't tend to enable malware scanning due to the added resources it requires. Currently, malware scanning for WordPress is inefficient; the two options available are either a plugin scanning your system or a malware scan done through a backup service where the malware scan is offloaded and done by the backup vendor on their servers. The ideal solution is that malware scanning is implemented on your hosting provider and done using an efficient scanning engine that only adds a small amount of overhead.
Security is important; ensure it's done efficiently and as uncomplicated as possible.
2 - Am I reading this correctly that you do not enable Fail2Ban or the 7G Firewall with GridPane
Am I reading this correctly that you do not enable Fail2Ban or the 7G Firewall? But that you do run the additional measure such as Block Comments, Block TrackBacks, etc. Obviously without the XMLRPC blocking as that is now done at Cloudflare.
I should update this article and be more specific. You have to consider every situation.
- Fail2ban
- /wp-admin protected with a Cloudflare managed challenge isn't going to see lots of automated traffic so Fail2ban won't have much todo. However, that doesn't mean that it's 100% accurate; some automated traffic or real people doing automation can still do damage. It'll be rare unless your site is a high-value target and worth the extra effort. So as a backup, I'd use Calvin's Fortress.
- User Logins - I'd look at Cloudflare Turnstile and Calvin's Fortress, again mostly because Calvin's will be more accurate than Fail2ban because it has more data due to being closer to the application. Also, Calvin's made it extremely performant. It's rare to find plugins that are like this; Calvin is a sicko when it comes to perfection.
- I hope that GridPane can develop a web server-based managed challenge similar to Cloudflare. Right now Fail2ban is only half way there, when someone is blocked, they are blocked at the server level and don't know that they're blocked as they get a generic browser error saying connection refused.
- I really do like the 7G firewall and modsec. It's just not managed by GridPane, you have to make up your own whitelists for common plugins. Or look for someone who has collected all the common whitelists in a Github repository and apply it server wide.
- Correct, I pick and choose what I feel is necessary, is easy to maintain, and does something measurable.
- For instance, Blocking the WordPress version number breaks lots of things in WordPress. It's not a good implementation but the only possible one. This needs to happen in the WordPress core, not as a mu-plugin. There are too many places where the WordPress version is used, and too many places it's exposed.
- Fun fact: I also run Wordfence for the WAF and live patching. Mostly because it's a pretty good WAF (not performant but decent). The live patching also helps when clients install plugins they've saved somewhere on Google Drive that is no longer in the WordPress repository. Lots of people hate WordFence, meh.
Historic Information
Cloudflare has announced that it will deprecate the legacy Cloudflare Firewall Rules on 02/28/2023. This means that any rules that were created using the old Firewall Rules UI will no longer be supported, and users will need to migrate to the new Firewall Rules UI before the deprecation date.
The Cloudflare Firewall Order and Priority (Deprecated)
There is no longer a firewall order and priority feature; the new Cloudflare Firewall has been replaced by Cloudflare Custom WAF Rules ordering evaluation.
As the title says, there is an order and priority within the Cloudflare Firewall. Here are some excerpts from the Cloudflare Firewall Rules Order Priority page.
You can use IP Access rules to allowlist requests under certain conditions, effectively excluding these requests from all security checks. However, allowing a given country code will not bypass WAF Managed Rulesets or WAF managed rules (previous version)Open external link.
The execution order diagram does not include products powered by the Ruleset Engine like the WAF or Transform Rules.
Keep this diagram in mind when you're troubleshooting, as you may find that your firewall rule might be correct, but there is an IP Access Rule or Rate Limiting Rule affecting traffic.
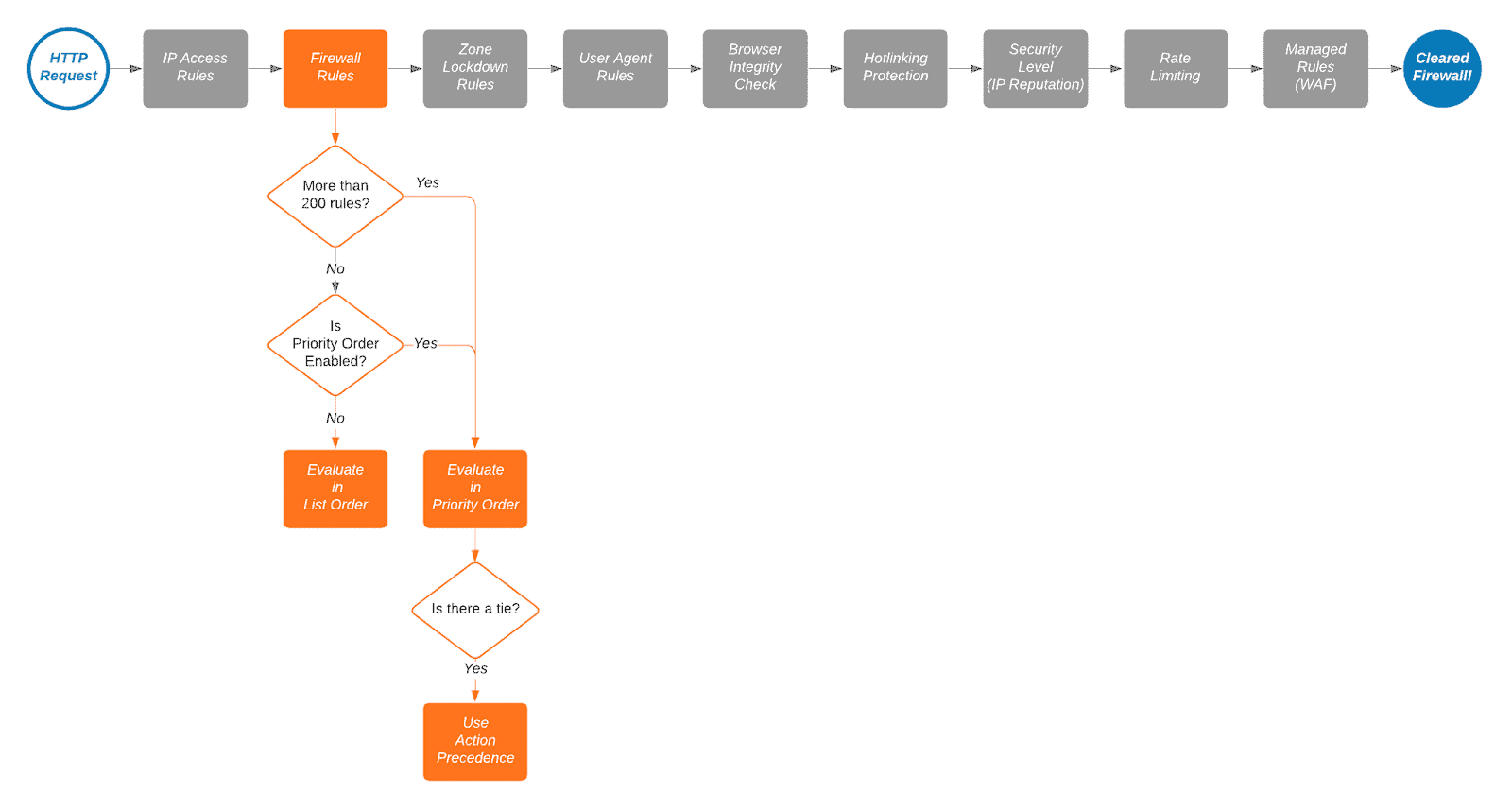
Cloudflare Firewall List Order and Rule Evaluation
Cloudflare's firewall rules are in list order; they're evaluated in the order they appear in the firewall rules list. You can drag and drop them into order as needed. Here is a nifty gif from the same page on Cloudflare's Developer's site.
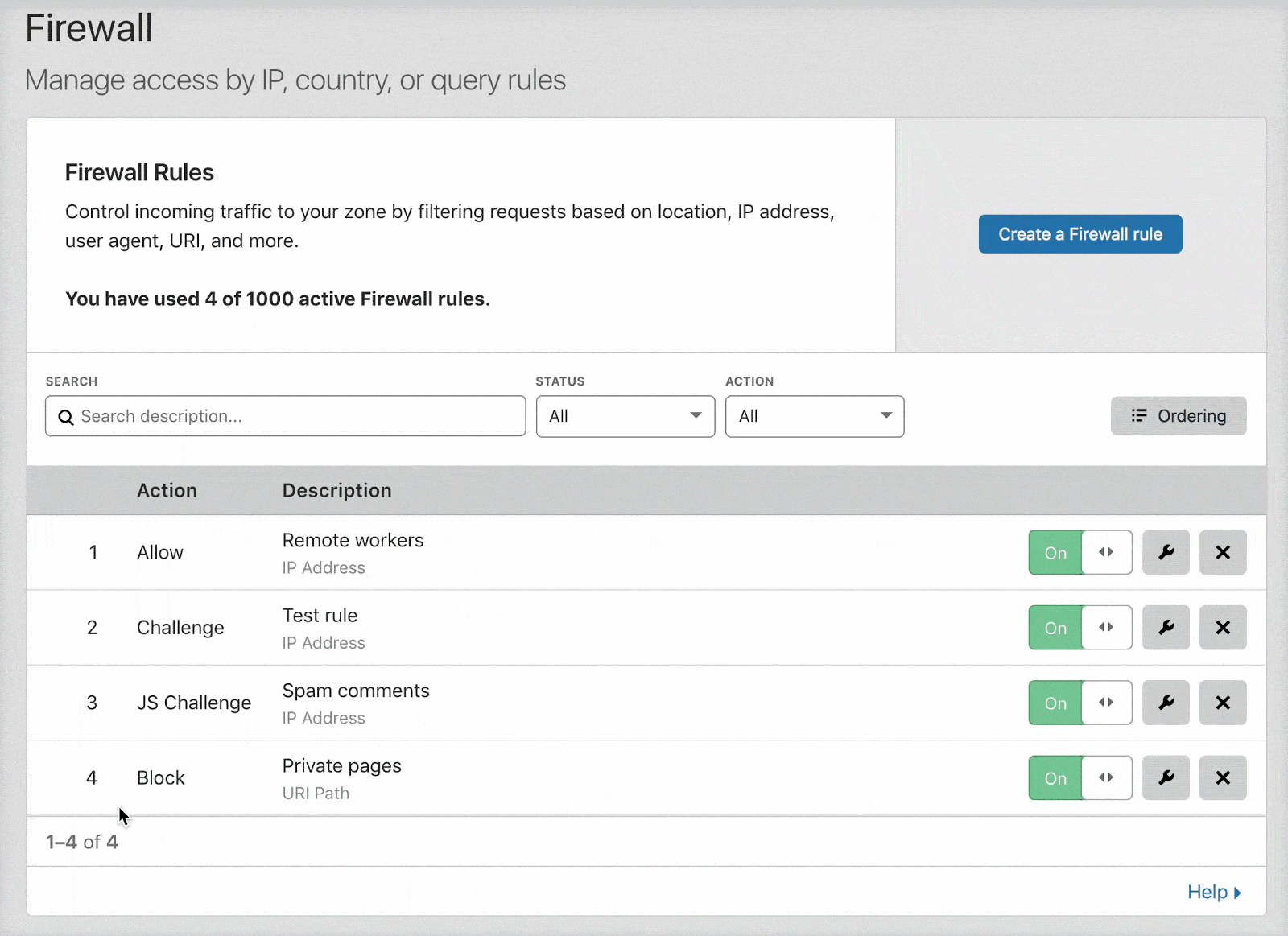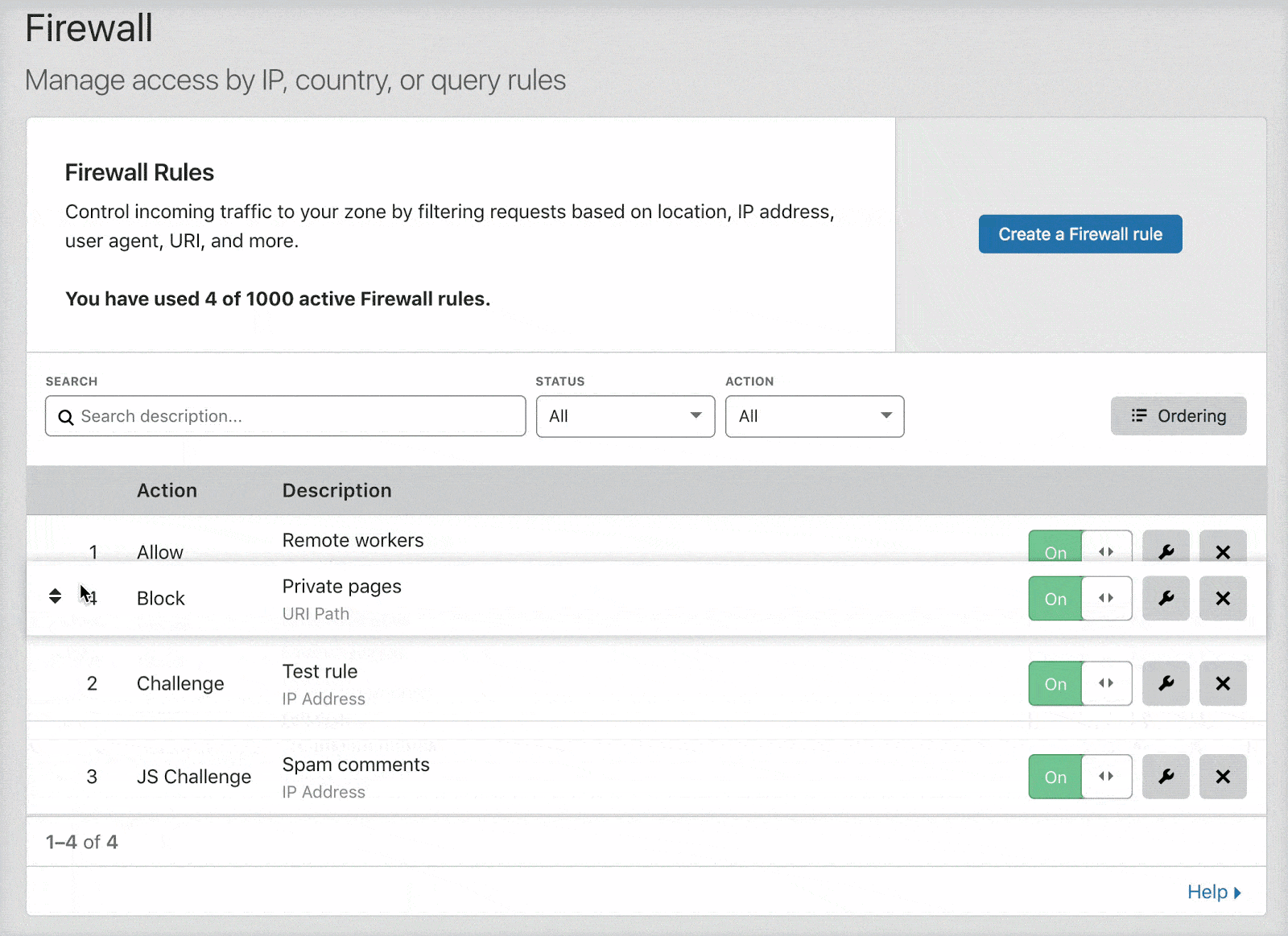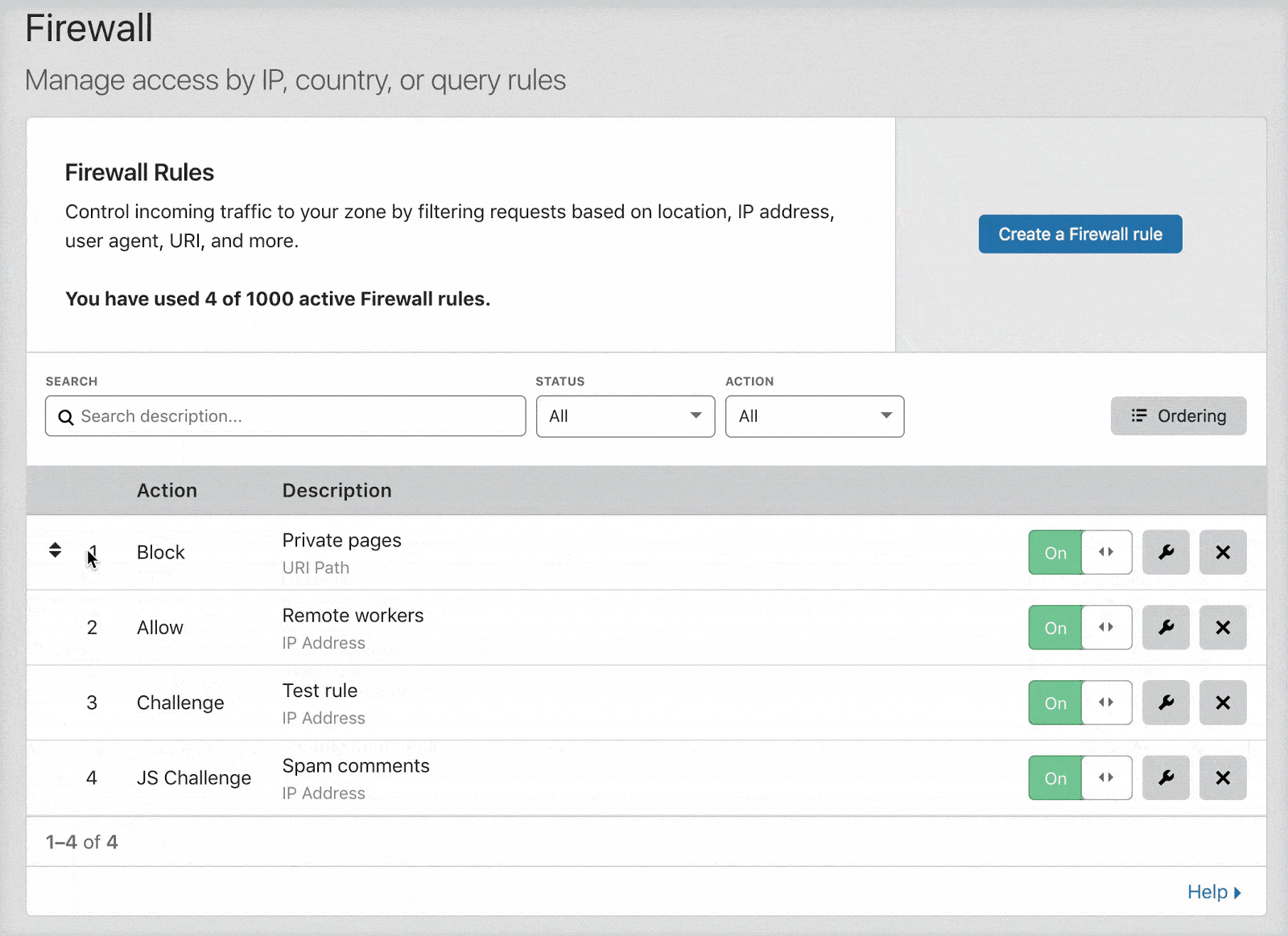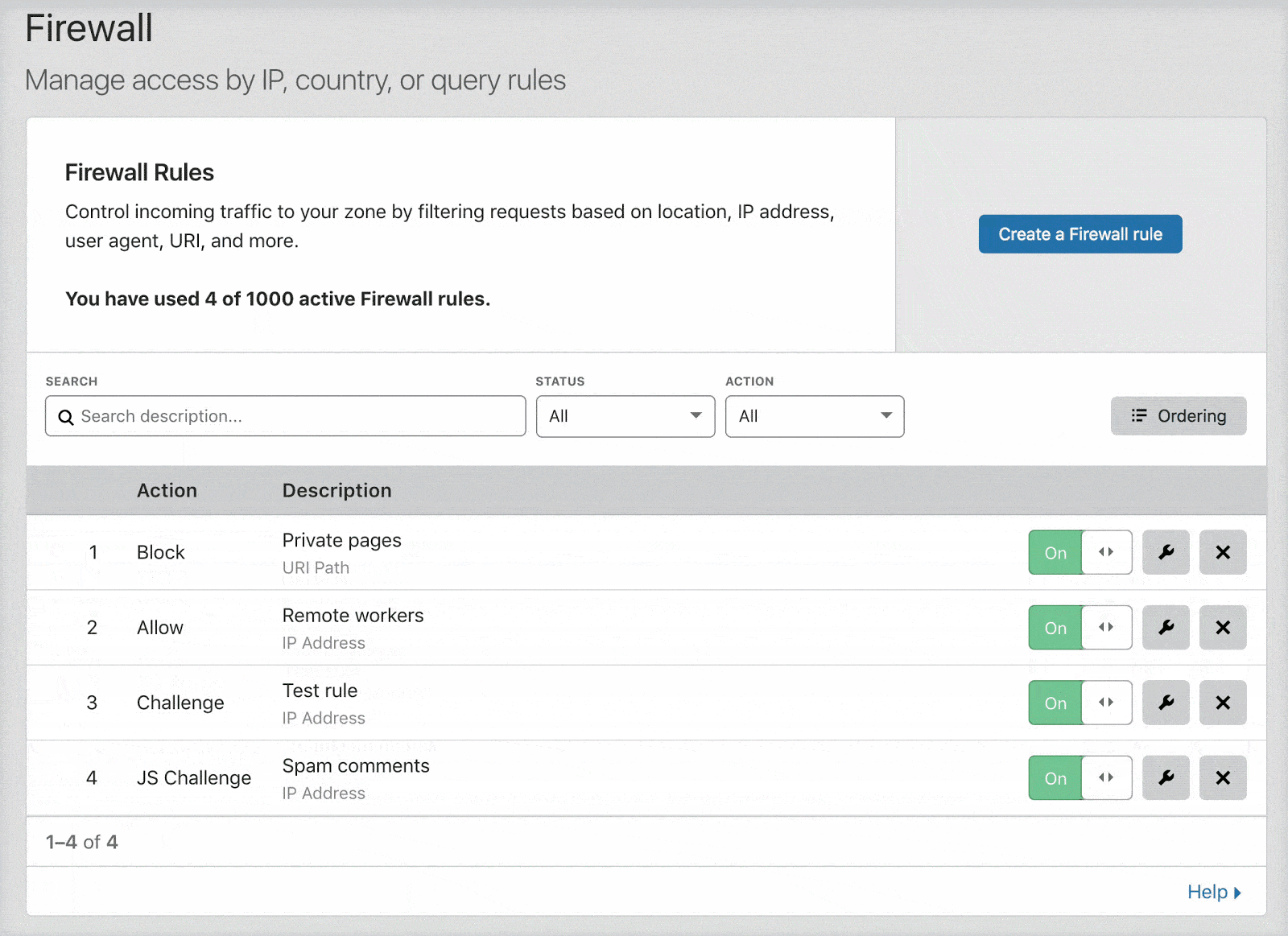
You can change the options for rule evaluation from the default "Order" which is drag and drop, to "Priority" by clicking the "Ordering" button on the right.
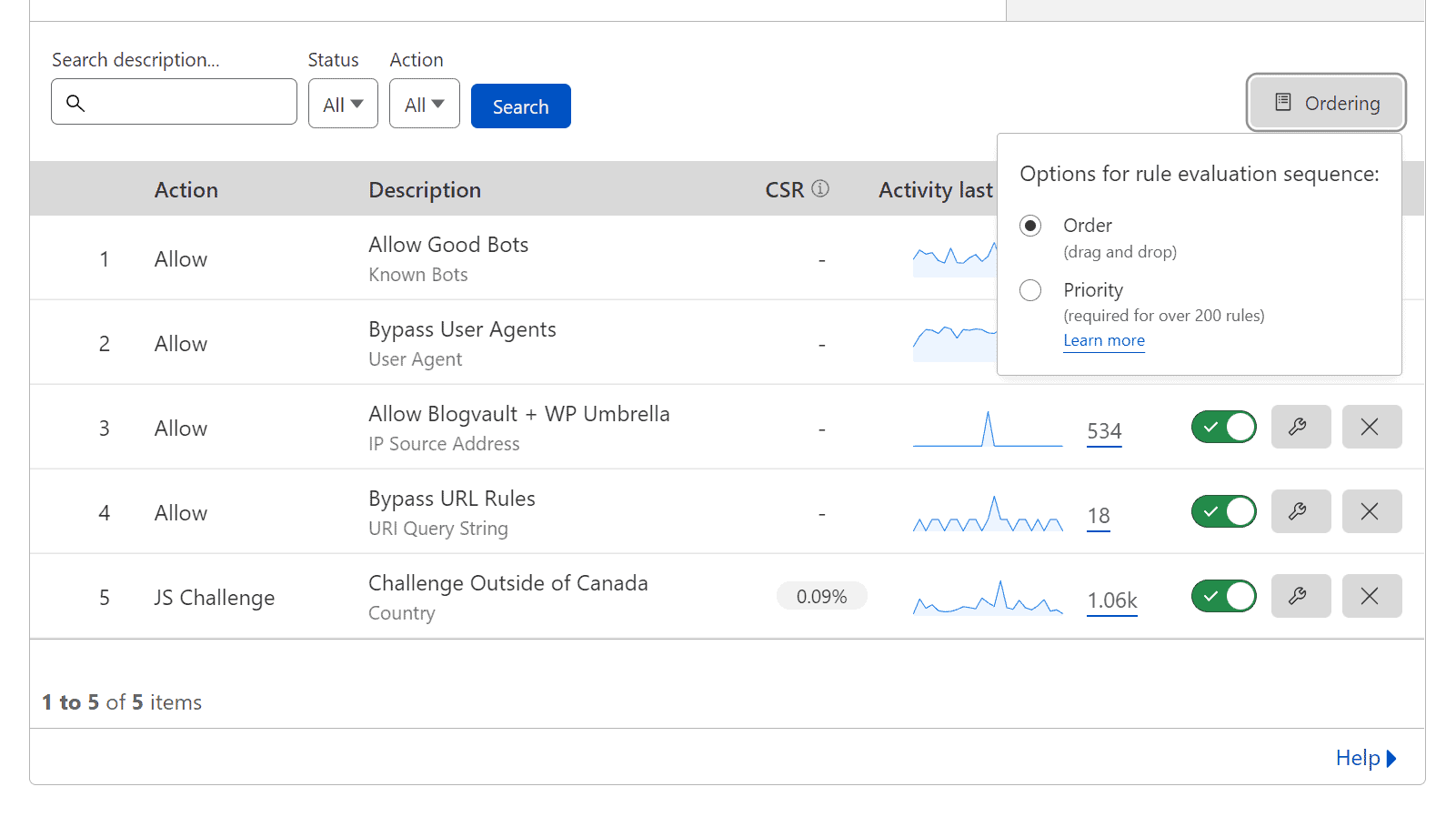
Drag and Drop vs Priority Ordering
I don't like taking something already written well, so here are some quotes from Cloudflare about Drag and Drop vs Priority Ordering.
By default, Cloudflare evaluates firewall rules in list order, where rules are evaluated in the order they appear in the firewall rules list. List ordering is convenient when working with small numbers of rules because you can manage their order by dragging and dropping them into position. However, as the number of rules grows, managing rules in list order becomes difficult. This is where priority order comes into play.
https://developers.cloudflare.com/firewall/cf-firewall-rules/order-priority/
When priority ordering is enabled, Cloudflare evaluates firewall rules in order of their priority number, starting with the lowest. If a request matches two rules with the same priority, action precedence is used to resolve the tie. In this case, only the action of the rule with the highest precedence is executed, unless that action is Log or Bypass (refer to Firewall rules actions for details). Priority ordering makes it a lot easier to manage large numbers of firewall rules, and once the number of rules passes 200, Cloudflare requires it.
https://developers.cloudflare.com/firewall/cf-firewall-rules/order-priority/
Cloudflare Firewall Rules Deprecated 02/28/2023
Cloudflare Firewall Rules are now deprecated. For most users, their firewall rules will now be displayed as WAF custom rules in the Cloudflare dashboard. In the future, you will no longer be able to manage firewall rules via Firewall Rules API or through firewall rules’ Terraform resources. All remaining active firewall rules will be disabled.
https://developers.cloudflare.com/waf/reference/migration-guides/firewall-rules-to-custom-rules/
Changelog
- 08-13-202
- Updated IP Access List section, and informed about the setting being deprecated.
- 12-16-2024
- Moved some information to historic information section.
- Updated rules to v2 which consildates allow rules and now only takes up four rules.
- 11-10-2023
- Changes Rule #1 Block to be Rule #2 and Rule #2 Allow to Rule #1
- Updated Allow to Skip due to Cloudflares change in how rules are generated.
- 06-15-2023
- Refined article a bit.
- Added in Question 2 for clarification on Question 1
- 06-14-2023
- Created a link at the top of the article to go right to the Cloudflare WAF rules.
- Updated the headings and small design changes.
- Added deployment via Terraform
- Added additional resources.
- 06-10-2023
- Added "/wp-admin/js/password-strength-meter.min.js" to by bypassed on "Rule 3 - Managed Challenge /wp-admin (Managed Challenge)"
- Added section on testing Cloudflare WAF using firewalker
- 04-06-2023
- Lots of changes to the structure and content of this article. It was patched together, so I've started to improve it further.
- Added section discussing Cloudflare WAF Custom rules replacing Cloudflare Firewall.
- Added section discussing Cloudflare WAF Managed Rules for Free and Pro
- Lots of updates, too many to list.
- 08-10-2022 - Improved rules overall, condensed rules and labelled them appropriately.
- 08-11-2022
- Fixed issue with an animated GIF showing how to drag and drop rules.
- Added a quote on how to use Cloudflare ordering and priority.
- Added "Google Crawl Errors" section
- Added Github repository for rules.
- 08-25-2022 - Blocked xmlrpc.php