Content Error or Suggest an Edit
Notice a grammatical error or technical inaccuracy? Let us know; we will give you credit!
Draft Warning
You’ve reached a draft 🤷♂️ and unfortunately, it’s a work in progress.
Introduction
This was posted on the GridPane Community, my response was so long and one that I’ve written many times before that I decided it deserved a blog post. I hope to update quite a few times so it’s perfect 😊
Can anyone give me a rundown of Gridpane WAF (6 or 7) vs the one offered by Cloudflare for an additional $20 a month? Is Cloudflare worth it?
Different types of WAF’s
Cloudflare as a WAF vendor has done a great job of explaining the different WAF’s.
A network-based WAF is generally hardware-based. Since they are installed locally they minimize latency, but network-based WAFs are the most expensive option and also require the storage and maintenance of physical equipment.
A host-based WAF may be fully integrated into an application’s software. This solution is less expensive than a network-based WAF and offers more customizability. The downside of a host-based WAF is the consumption of local server resources, implementation complexity, and maintenance costs. These components typically require engineering time, and may be costly.
Cloud-based WAFs offer an affordable option that is very easy to implement; they usually offer a turnkey installation that is as simple as a change in DNS to redirect traffic. Cloud-based WAFs also have a minimal upfront cost, as users pay monthly or annually for security as a service. Cloud-based WAFs can also offer a solution that is consistently updated to protect against the newest threats without any additional work or cost on the user’s end. The drawback of a cloud-based WAF is that users hand over the responsibility to a third party, therefore some features of the WAF may be a black box to them. (A cloud-based WAF is one type of cloud firewall; learn more about cloud firewalls.)
Perishable Press/GridPane 7G/6G Firewall
The Perishable Press 7G/6G firewall by Jeff Star is used by GridPane and is a set of static firewall rules for Apache/OLS&LSWS/Nginx. It’s considered a host-based WAF but is not susceptible to performance issues because it uses Nginx’s configuration rules, which are performant. The Perishable Press 7G/6G firewall protects against known malicious requests and attacks on your WordPress site or server. You can read more about it here
The 7G Firewall offers lightweight, server-level protection against a wide range of malicious requests, bad bots, automated attacks, spam, and many other types of threats and nonsense.
7G Updates
The 7G firewall hasn’t been updated since 2021-11-03 isn’t updated frequently. For instance, at the time of this article writing, the last update was v1.5 on 2021-11-03, and since then, v1.6 was released on 02-06-2023. So around 3 months between updates, which is good, but not ideal as other solutions are updated more frequently and require no action. With 7G, you must download and implement the new rules. You can see the changelog for 7g at https://perishablepress.com/downloads/7G-Changelog.txt
7G False Positives
Something to consider is false positives that will affect the functions of a WordPress site. This does occur and requires that these functions are allowed past the 7G/6G firewall using the appropriate code. This can require extra care and feeding if you have a site with plugins adding front and backend functionality. Some people maintain bypass rules for the many situations they’ve encountered, which has taken time to create. This might seem like a hurdle, but it’s better than no protection at all, especially on a brochure site, than on an e-commerce site. Every site is unique, and you might find more issues on one than the other. Extending the 7G firewall is possible if you want to get dirty with coding.
8G Firewall Beta
The 8G Firewall beta was released on 02/16/2023 and is available for download.
8G Notes
Any 8G-related notes will be added/updated here..
- Only use 7G or 8G, not both
- 8G is modular: each section can be removed/added as desired
- 8G is designed to work flawlessly with WordPress or any other non-WP site
- 8G adds new “HTTP COOKIE” rules
- Please report any strings or user agents that should not be blocked
- Always test well before going live and report any bugs or issues
- Other 8G-related notes will be added here..
Cloudflare WAF
Cloudflare is a Cloud-based WAF that has been around since 2009 and protects a large portion of the internet. You can read more about Cloudflare here

Cloudflare works the same; it has its own WAF rules for the free plan, and if you upgrade, you get access to managed rules written by Cloudflare. The Cloudflare rules are static. However, they’re constantly updated and improved and available instantly by Cloudflare. You don’t need to worry about updating, only if there are issues with false positives.
If you do have an issue with a false positive, you can put in a bypass rule to address the false positive. This is done through the web UI versus through scp or SSH in a file that has a specific coding structure like Perishable Press 7G. Granted, the UI does have the option to enter in expressions (code) you most likely will use the UI’s rule builder most of the time. Cloudflare’s WAF allows for custom rules (5 on free), and you can implement significant measures to stop attacks and automated resources-based attacks. We’ve written a great article on how to do just that.
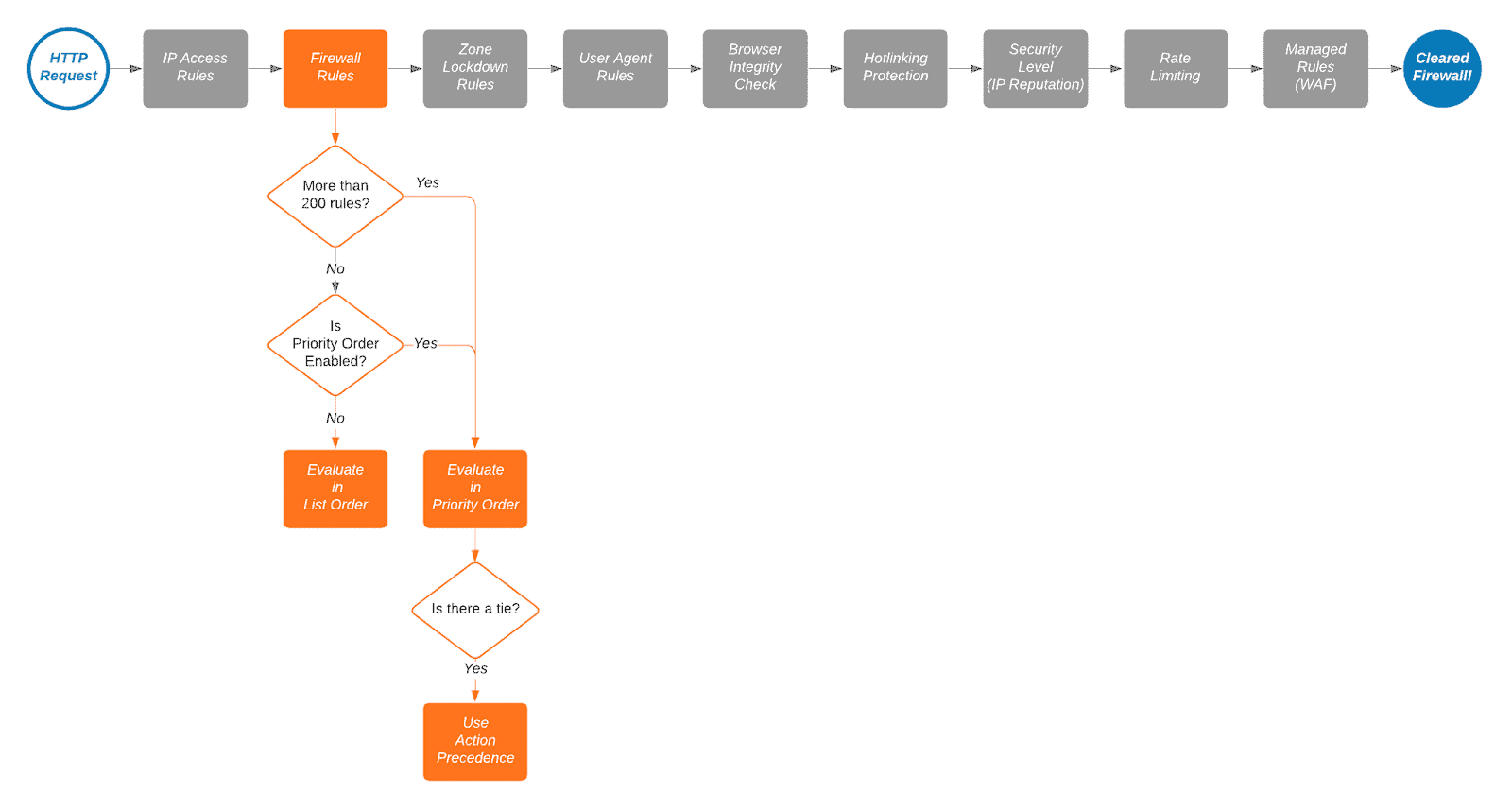
We also have several other Cloudflare articles you might be interested in.
Other Cloudflare Guides
- Rant, Cloudflare Bot Fight Mode doesn’t provide firewall bypass or whitelist?
- Using Cloudflare Without Changing your Name Servers
- Cloudflare 520 Errors Explained and Investigated
- Secure, Protect and Lock Down your WordPress site with Cloudflare Custom WAF Rules (was Firewall Rules)
- Protecting the WordPress Admin Login with Cloudflare
- Testing and Reviewing Cloudflare Firewall and WAF Rules
- Common WordPress Cloudflare WAF (Web Application Firewall) Rules
The most significant difference that makes Cloudflare stand out is it’s verified bots filter, country detection and connection challenges. Whenever a connection is made to your website by a device, Cloudflare can tell if it’s a verified bot (Google Crawler), from a specific country and ask the device to verify it’s not an automated bot.
This allows for some magical things to happen, you can allow all verified bots, but block bad bots that are potentially utilizing your server resources that could be used for a natural person. You can block everyone outside of your specific website geographical service area, require that they go through the Cloudflare Managed Challenge or Javascript Challenge. Both are explained below.
Managed challenges are where Cloudflare dynamically chooses the appropriate type of challenge based on the characteristics of a request. This helps avoid CAPTCHAs, which also reduces the lifetimes of human time spent solving CAPTCHAs across the Internet.
https://developers.cloudflare.com/fundamentals/get-started/concepts/cloudflare-challenges/
With a JS challenge, Cloudflare presents challenge page that requires no interaction from a visitor, but rather JavaScript processing by their browser. The visitor will have to wait until their browser finishes processing the JavaScript, which should be less than five seconds.
https://developers.cloudflare.com/fundamentals/get-started/concepts/cloudflare-challenges/
This opens up a ton of opportunity, and ultimately allows you to protect your WordPress admin from being automatically brute forced and offloads this to Cloudflare versus using your server’s resources or time spent setting up and maintaining a plugin or service like fail2ban.
Conclusion
If you need protection now and don’t have a Cloudflare setup, the 7G firewall works excellently. If you want to go a step further, Cloudflare provides the best protection available for a WordPress site for free, even upgrading to the Pro plan that includes more Clouldflare-managed WAF rules and APO is a great price for $20/month.
Changelog
- 03-20-2023 – Updated verbiage in-regards to 7G firewall updates, and added section about 8G Firewall beta.
- 03-08-2023 – Grammar and visual changes.
- 09-26-2022 – Published





