Table of Contents
- What’s card testing or carding?
- Preventing Card Testing in WordPress, WooCommerce and More
- 6. Protect and Lock Down WordPress using Cloudflare
- Other Cloudflare Guides
- Conclusion
- Other Options
- Change Log
Content Error or Suggest an Edit
Notice a grammatical error or technical inaccuracy? Let us know; we will give you credit!
What’s card testing or carding?
Card Testing, sometimes called Carding, is the act of testing stolen credit card information against a payment processor to verify the stolen information is valid. The targets of card testing or carding are usually online stores that allow for small purchases and have low security.
Preventing Card Testing in WordPress, WooCommerce and More
I’ve compiled a list of options for preventing card testing or carding in WooCommerce. The options provided are suggestions, and any referenced plugin and service is simply a match, not a general endorsement. Do your research!
Multiple WordPress plugins can process credit cards; this guide will apply to some but may not work with all. Ensure you test the methods below before implementing them into your production site.
1. Enable Credit Card Fraud Detection (ex 3D Secure)
If your payment gateway or payment processor supports additional fraud detection, ensure it’s enabled and working. An example of this is 3D Secure, which most processors support.
Some fraud detection features may be disabled at your processor, and you will need to log in and enable these fraud detection options. You must also ensure that the WooCommerce payment plugin you’ve chosen supports your payment processors’ fraud detection. In the case of some older plugins, technology such as 3D Secure is supported by the payment processor but not implementing by the plugin vendor.
Enable CVV Checking
This is a standard in the industry, but some stores still don’t enable CVV checking. I don’t see why you wouldn’t enable this.
Enable Postal Code Checking
I know this can be problematic, but if you’re being attacked and paying for refunds or worse chargebacks, a little friction for your customers saves you money in the long run.
2. Add a Captcha (Easiest and Best Method)
This might be counterintuitive as the checkout experience is supposed to be quick and easy. This will help if you require customers to create an account, and they can save their billing details. Anything that makes it easier for the customer will make it easier for the attackers. You can add a captcha to the WooCommerce login, registration, and forgot your password pages. There is also an option to add a captcha on the checkout. However, it’s an effective method.
Here are some WordPress captcha-based plugins in no official order.
3. Block Countries with a WordPress Plugin
If your store only services a handful of countries, you can block all countries it doesn’t service from checking out. This can be done quickly with a plugin and typically an IP-to-country database like Maxmind. This database maps internet IP addresses to countries and is pretty accurate. You can download their database or use their API; they have a free and paid plan.
Here’s a list of WordPress plugins that allow you to block specific countries in no official order.
- MalCare
- WordFence – * Paid version only
- iQ Block Country
- IP2Location Country Blocker
4. Block Countries with your Web Server
Nginx
You can block countries using Nginx’s GeoIP module and some configurations. Here’s an example guide
LiteSpeed
You can block countries using Litespeed’s GeoLocation support which allows you to use Maxmind or IP2Location databases. You can read more on their website.
5. Block Countries with Cloudflare
You can set up Cloudflare rules to block specific countries from accessing your sites. Here are a couple of examples; you can add these to the “Edit Expression” section of the firewall rule versus using the dropdowns.
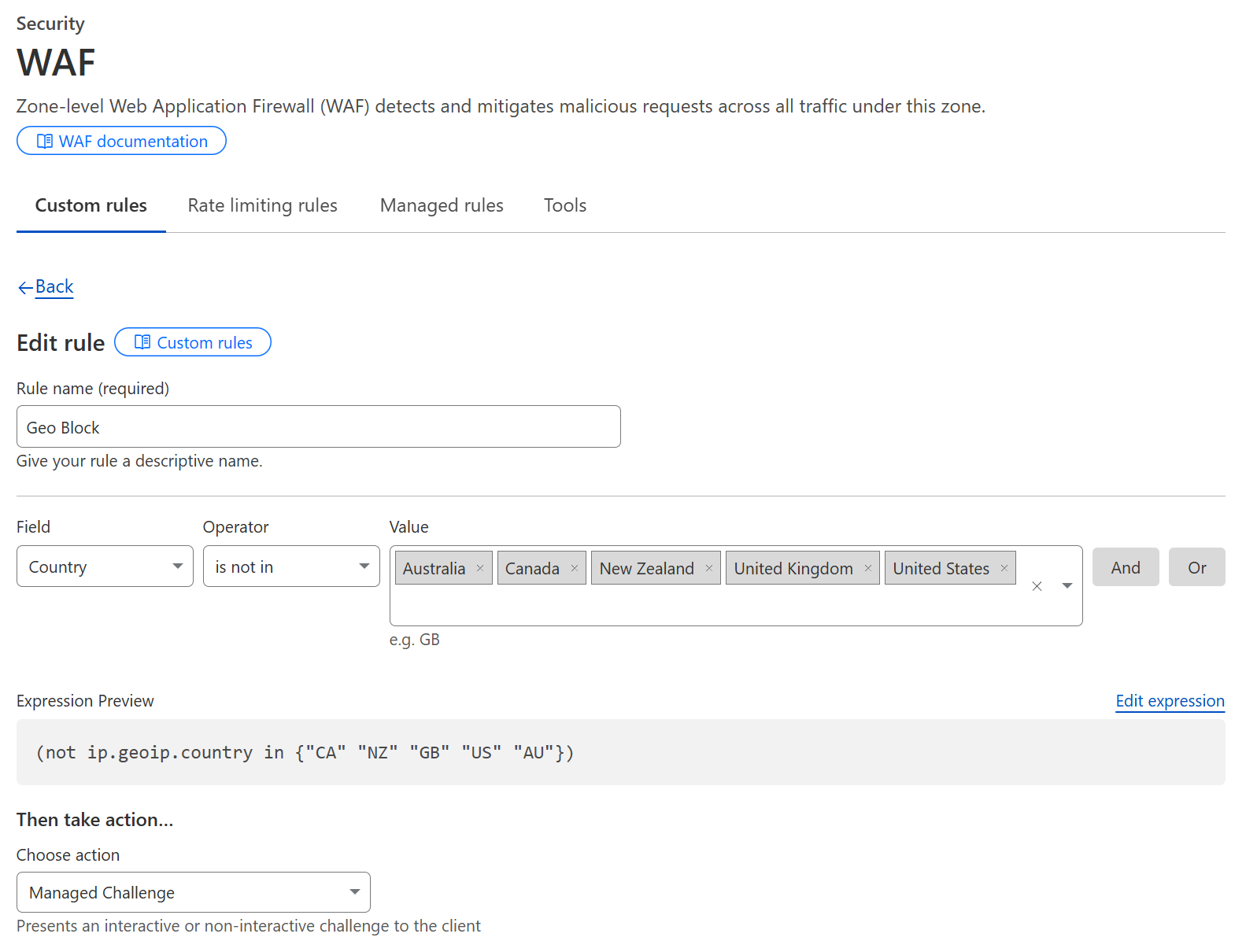
Cloudflare Block Specific Countries
(ip.geoip.country eq "RU") or (ip.geoip.country eq "HK")
Cloudflare Block all countries but allow only specific countries
(ip.geoip.country ne "US") or (ip.geoip.country ne "CA")
There is further Cloudflare rules that you can use on your site at wpguide.io
6. Protect and Lock Down WordPress using Cloudflare
You can go further and lock your entire site down using Cloudflare easily. This is the ultimate protection from automated attacks resulting in wasted resources and carding attacks.
Managing WP Cloudflare Rules
Troy Glancy from Web Agency Hero Cloudflare Rules
Other Managing WP Cloudflare Guides
Other Cloudflare Guides
- Rant, Cloudflare Bot Fight Mode doesn’t provide firewall bypass or whitelist?
- Using Cloudflare Without Changing your Name Servers
- Cloudflare 520 Errors Explained and Investigated
- Secure, Protect and Lock Down your WordPress site with Cloudflare Custom WAF Rules (was Firewall Rules)
- Protecting the WordPress Admin Login with Cloudflare
- Testing and Reviewing Cloudflare Firewall and WAF Rules
- Common WordPress Cloudflare WAF (Web Application Firewall) Rules
7. Cloudflare Bot Fight Mode
There isn’t a specific feature of Cloudflare that tackles card testing directly. There are, however, some necessary settings you should consider enabling or configuring. One of them is Bot fight mode which can help if your site is being card tested by bots versus humans.
WARNING
Bot fight mode will block Zapier and WordPress URL-based manual cron URLs. As well as external services that require accessing your site via a URL. Furthermore, Bot Fight Mode may block indexers or crawlers.
When you enable Bot Fight Mode, it will sometimes block external services that are trying to pull data or trigger an event. Two popular examples would be a third-party service like Zapier or a manual WP-Cron that uses curl and the wp-cron.php URL ( See: Replacing WordPress WP Cron with Manual Cron (URL and PHP Method))
Two clients had Bot Fight Mode turned on, and the following happened.
Cloudflare Bot Fight Mode Issue #1 – Zapier
One client was using the WooCommerce Zapier plugin by OM4. Unfortunately, a Zap had failed and the client tried to confirm that the Zapier connection was working. This was blocked and resulted in other issues. If you’re using Zapier with WooCommerce, always set up appropriate Zaps to monitor failed zaps and when zaps are turned off.
Cloudflare Bot Fight Mode Issuer #2 – WP-Cron
Another client was using GridPane for their site and had GP-Cron enabled. Unfortunately, the GP-Cron uses the URL method and will reach out to the client’s site using the URL https://domain.com/wp-cron.php?doing_wp_cron
Since domain.com is pointed at Cloudflare, the request goes through Cloudflare first and then gets blocked by Bot Fight Mode. Even though the request is coming from the original server. This ended up causing issues with WooCommerces Subscriptions not firing correctly.
You can whitelist Cloudflare’s Bot Fight Mode, but not by the user agent or request URL. You can only whitelist the origin server’s IP. And if you move your site around, you must remember to change this IP Addres.
6. Rate Limiting or Request Throttling
Rate limiting or throttling WooCommerce orders is another option that will not stop card testing completely but will make it harder for automated attacks to occur.
Rate Limiting and Request Throttling Plugins
- Nexcess Limit Orders Plugin – A plugin by Nexcess limits WooCommerce orders overall and not by a specific customer or other variables such as IP Address. You can learn more about the plugin on the WordPress plugin directory.
- YITH WooCommerce Anti-Fraud Plugin – Another plugin by YITH called YITH WooCommerce Anti Fraud does have a setting “Attempt count check” which will only allow a certain amount of orders to occur within a specific time period based on IP Address. This is very useful, but some attackers will use different IP addresses. You can read more about the plugin on the YITH website.
- Checkout Rate Limiter Plugin – I found out about this plugin from a Facebook post discussing card-testing attacks. This plugin will rate limit orders based on IP address. I haven’t tested it, so please test it before implementing it into production.
Cloudflare Rate Limiting
I don’t have experience with this feature; you can set up Rate Limiting rules on paid Cloudflare plans. This would allow you to rate limit IPs and only allow a specific number of connections per IP in a given time frame.
7. Anti-spam Plugins
Looking for some more suggestions here that protect WooCommerce checkouts.
- WP Armour – Honeypot Anti Spam – There is a free and paid pro version, and it does work to help stop automated attacks.
- OOPSpam – A newer company geared towards filtering abuse and spam on many different platforms. The WordPress plugin works for WordPress core and WooCommerce. https://www.oopspam.com/blog/spam-protection-for-woocommerce
- Cleantalk (Affiliate Link)—I was hesitant to suggest Cleantalk because, based on some Facebook group discussions, it has issues on sites with large databases and heavy traffic. However, it does have a decent block rate. Unfortunately, when an order is blocked, a generic Forbidden message is shown, and you have to pay extra to customize this message.
8. Require Account Registration, Email or SMS Account Verification
Requiring users to create an account before checking out or verify their emails before ordering is another method to slow down automated card testing attacks. However, this presents a delay in a customer checking out. Especially if the verification email or SMS doesn’t arrive in time or is marked as spam.
9. WooCommerce Fraud Detection Plugins
There are a couple of Fraud Detection or Anti Fraud plugins available. Some are simply there to let you know that an order is likely to be fraudulent, some will block orders.
Here’s a list of Fraud Detection and Anti Fraud Plugins in no specific order.
- WooCommerce Anti-Fraud – Requires a third-party integration.
- Woo Manage Fraud Orders
- YITH WooCommerce Anti Fraud
- FraudLabs Pro for WooCommerce
- Fraud Prevention Plugin for WooCommerce
10. Reviewing Logs
Payment Processor Logs
Always check your payment processor logs to verify where the charges are being created. A staging site may exist with production API keys, or your site was hacked, and the API keys were stolen. Most payment processors will have further details in their logs with additional information.
Server Access Logs
Double-check your site’s access logs with your payment processor logs and ensure everything lines up. If not, the charges may not come from your site but instead through another method. Typically you should see the attackers going through the checkout, however, if the attacker has found a way to trigger orders through another method which bypasses your checkout, you will see lots of POST requests to a specific URL. If this is the case, you may need to review your sites plugins and see if a specific plugin is poorly coded allowing attackers to bypass the checkout security.
Checking Stripe Payment Logs
Here’s a quick way to check your Stripe payment logs. Once logged into Stripe, find a fraudulent payment. Then scroll down to “Events and Logs”, click on the first event that usually states, “A request to create a Paymentintent completed”. Click on “View Log Details” as per the screenshot below.

You will then be presented with a bunch of information that helps confirm where the charges were initiated. Unfortunately this screenshot has been redacted, but will confirm the screen that you should be looking for.

11. Rotate your Payment Processor API Keys
This has often been mentioned in many Facebook groups, and I suggest doing this at least once. You can rotate your payment processor API keys anytime by logging into your payment processor admin interface. It’s possible that the attackers have gotten access to your API keys through many methods and are using your payment processor directly and bypassing your websites checkout.
12. Restrict IP Access at your Payment Processor
Some payment processors will allow you to restrict access to their API and your API keys based on IP Address. Reach out to your payment processor for more information
Conclusion
There are multiple methods and solutions to block card testing or carding. However, each store is different, and some can get by with simple and accessible solutions, while others might need more protection. Make sure you do your research on the above-linked plugins.
Other Options
There are several other options that I haven’t detailed in this article, please let me know if I’ve missed any, and I will update this article.
Change Log
- 12-27-2024 – Removed duplicate text in section 7 and added OOPSpam
- 10-22-2023 – Updated the plugin name to WP Armour – Honeypot Anti Spam
- 03-08-2023 – Clean up of visuals and grammar.
- 11/29/2022 – Small grammar and wording update, added Cloudflare Turnstile, added rotate payment processor keys, added restrict IP access at your payment processor, improved check logs section, added cvv and postal code checking, added honey pot armour.
- 11/02/2022 – Overhaul of content, added Checkout Rate Limiter Plugin and checked stripe logs.
- 08/27/2021 – Added more details about Cloudflare Bot Fight Mode and how it will block WP-Cron and Zapier.
- 07/08/2021 – Added FAQ about Cloudflare Bot Fight Mode.
- 10/26/2021 – Added information on using Cloudflare to block countries.
- 02/08/2021 – Added Cloudflare Rate Limiting
- 03/23/2022 – Updated link to Nexcess Order Limiting








