This page has had its content updated on March 27, 2024 EDT by Jordan
Content Error or Suggest an Edit
Notice a grammatical error or technical inaccuracy? Let us know; we will give you credit!
So you might be here because you either searched Google for maldet or you’re a GridPane customer looking to get more information about maldet and what it does.
Background on Linux Malware Detect, LMD or Maldet
I’ve always known about maldet, but never got the opportunity to use it. I’ve always searched and cleaned manually via SSH using tcsh/zsh shell. It took time, but also added a human element to it where I could see things a scanning engine couldn’t.
There are alternatives to maldet that you can check out.
- Wordfence CLI – https://github.com/wordfence/wordfence-cli
- Rootkithunter (Rootkit Related) – https://rkhunter.sourceforge.net/
Common Maldet Tasks
Running a Maldet Scan
To run a Maldet scan on a specific directory, you can use the following command, replacing /path/to/directory with the actual path of the directory you want to scan
maldet --scan-all /path/to/directory
If you want to scan your entire system, you can replace /path/to/directory with /.
Viewing Scan Reports
After the scan completes, Maldet will provide a report ID. You can view the detailed report of the scan results with the following command, replacing report_id with the actual report ID provided:
maldet --report report_id
Updating Maldet and Definitions
It’s important to keep Maldet and its malware definitions updated. You can update Maldet and its signatures using the following command
maldet -u maldet -d
Quarantine Detected Threats
If Maldet finds any threats, you can opt to quarantine them. Maldet may automatically suggest this, or you can manually quarantine files by using the -q flag followed by the report ID:
maldet -q report_id
Configuring Maldet
Maldet can be configured to suit your needs. Its configuration file is usually located at /usr/local/maldetect/conf.maldet or /etc/maldetect/maldet.conf, depending on your installation. You can edit this file to change various settings, such as email notifications, quarantine options, and scan options.
Example Scan
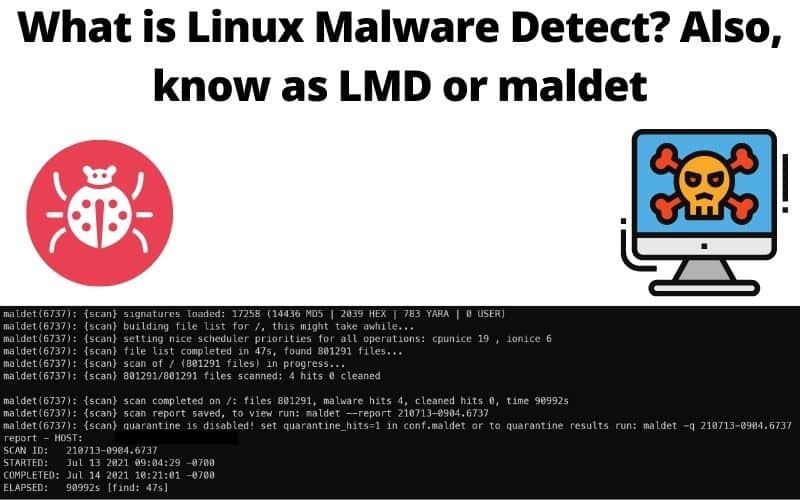
The following is a recent scan done on July 13th 2021, I’ve removed the server name and full paths to the malware for privacy concerns.
Scanning /var/www/ all sites with -maldet-scan
Scanning everything, this might take some time
Linux Malware Detect v1.6.4
(C) 2002-2019, R-fx Networks <proj@rfxn.com>
(C) 2019, Ryan MacDonald <ryan@rfxn.com>
This program may be freely redistributed under the terms of the GNU GPL v2
maldet(6737): {scan} signatures loaded: 17258 (14436 MD5 | 2039 HEX | 783 YARA | 0 USER)
maldet(6737): {scan} building file list for /, this might take awhile...
maldet(6737): {scan} setting nice scheduler priorities for all operations: cpunice 19 , ionice 6
maldet(6737): {scan} file list completed in 47s, found 801291 files...
maldet(6737): {scan} scan of / (801291 files) in progress...
maldet(6737): {scan} 801291/801291 files scanned: 4 hits 0 cleaned
maldet(6737): {scan} scan completed on /: files 801291, malware hits 4, cleaned hits 0, time 90992s
maldet(6737): {scan} scan report saved, to view run: maldet --report 210713-0904.6737
maldet(6737): {scan} quarantine is disabled! set quarantine_hits=1 in conf.maldet or to quarantine results run: maldet -q 210713-0904.6737
report - HOST:
SCAN ID: 210713-0904.6737
STARTED: Jul 13 2021 09:04:29 -0700
COMPLETED: Jul 14 2021 10:21:01 -0700
ELAPSED: 90992s [find: 47s]
PATH: /
TOTAL FILES: 801291
TOTAL HITS: 4
TOTAL CLEANED: 0
WARNING: Automatic quarantine is currently disabled, detected threats are still accessible to users!
To enable, set quarantine_hits=1 and/or to quarantine hits from this scan run:
/usr/local/sbin/maldet -q 210713-0904.6737
FILE HIT LIST:
{HEX}php.malware.magento.598 : wp-content/themes/azul/404.php
{HEX}php.nested.base64.648 : wp-content/plugins/wp-page-numbers/stylish/img/pogey.php
{HEX}php.malware.magento.598 : wp-content/themes/azul/404.php
{HEX}php.nested.base64.648 : wp-content/plugins/wp-page-numbers/stylish/img/pogey.php
Maldet Coverage for Malware
As with any malware tool, coverage will vary, maldet doesn’t have full 100% coverage and most scanners wont. I’d say Maldet has 80% coverage of malware, detecting malware older than a year, but that’s creeping into 1.5 years now.
Change Log
- 03-27-2024 – Took out of draft, added some common tasks for maldet and maldet coverage for malware. Added wordfence-cli and rootkithunter.
This page has had its content updated on March 27, 2024 EDT by Jordan