Table of Contents
Content Error or Suggest an Edit
Notice a grammatical error or technical inaccuracy? Let us know; we will give you credit!
DISCLAIMER
The following commands change how your GridPane server functions. This may void any support provide by GridPane, use at your own discretion. If you contact GridPane support, inform them that you made these changes.
08-25-2023 – This article pertains to the Ubuntu 18/20 instances of GridPane, which in 2023 will both be retired eventually due to Ubuntu 22 instances being available. Which comes with a jail shell, so SSH and su from root are available but I’m not aware if SSH forwarding is available.
Allowing SSH Access to GridPane System Users
Notice
If you change a system user’s password or add an SSH key, the changes you make below will be reverted.
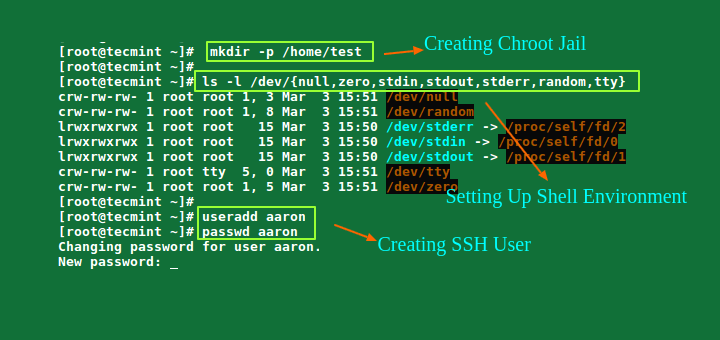
If you’re looking to give a developer or user access to SSH instead of the default SCP-only that GridPane institutes for each system user. Then you will need to follow these instructions.
Step 1 – Removing SFTP Restriction Configuration
GridPane restricts users to only SCP connections by using the sshd configuration “ForceCommand”. Furthermore, to restrict access to files outside of the system users’ home directory, the sshd configuration option “ChrootDirectory” is used.
The configuration is within /etc/ssh/sshd_config, and below is an example
#CONFIG FOR USER=wpinfo
Match User wpinfo
ForceCommand internal-sftp
ChrootDirectory /home/wpinfo
PasswordAuthentication yes
X11Forwarding no
AllowTcpForwarding no
#ENDCONFIG FOR USER=wpinfo
You can simply comment out the “ForceCommand internal-sftp” option on line 3 or remove the configuration for the entire user. And then restart ssh by typing the following.
systemctl restart ssh
Step 2 – Removing Chroot Configuration
If you now try to log in via SSH as a system user, you will be greeted with the following error.
Last login: Wed Mar 25 04:14:22 2020 from 1.1.1.1 /bin/bash: No such file or directory Connection to srv01.managingwp.io closed.
This is because when you log in as a GridPane system user, you’re chrooted into your home directory. You can read more about chroot, how to set it up and extend it further at https://www.tecmint.com/restrict-ssh-user-to-directory-using-chrooted-jail/
We can comment out or remove line 4 within the sshd config for the specific system user. Eventually, the configuration file looks like this if you also previously removed the SFTP restriction configuration in this article (line 3).
#CONFIG FOR USER=wpinfo
Match User wpinfo
# ForceCommand internal-sftp
# ChrootDirectory /home/wpinfo
PasswordAuthentication yes
X11Forwarding no
AllowTcpForwarding no
#ENDCONFIG FOR USER=wpinfo
Step 3 – Enabling Visual Studio Code Remote SSH
If you’re using Visual Studio Code Remote SSH extension.
You will need to uncomment an additional line to be able to utilize this Visual Studio code extension. The Remote SSH extension for Visual Studio Code utilizes SSH Forwarding, which is disabled by default for GridPane system users. So uncomment AllowTcpForwarding no like so
#CONFIG FOR USER=wpinfo
Match User wpinfo
# ForceCommand internal-sftp
# ChrootDirectory /home/wpinfo
PasswordAuthentication yes
X11Forwarding no
# AllowTcpForwarding no
#ENDCONFIG FOR USER=wpinfo
Step 4 – Restart the SSH daemon.
You need to restart the SSH daemon for the changes to take effect.
systemctl restart ssh
Now you should be able to use Putty or ssh command to login as the system user without any issues. Until you want to create files in your home folder, that’s another issue.
Allowing SU to User from Root
UPDATE 03/24/2020
If you’ve ever tried to ‘su -‘ into a GridPane system user, you’ll see the following error. Sometimes this is all I do from the root user versus logging into each individual user. I will explain my reasoning one day. If you want to SSH into a GridPane system user, I’ve added it to the end of this article.
❯ su - user Cannot execute /bin/bash: Permission denied
Step 1 – Checking ACL restrictions on /bin
The main reason you’re having the issue above is an ACL permission that was added to /bin and /dev that restricts you from starting a shell within /bin or accessing /dev. The latter is more of an annoyance each time you run a command, so I thought I would add it in. This is due to /bin being restricted by an ACL
❯ getfacl /bin getfacl: Removing leading '/' from absolute path names # file: bin # owner: root # group: root user::rwx group::r-x group:GridPane-System-Users:r-- mask::r-x other::r-x
Step 2 – Remove ACL on /bin
You can remove the ACL, and then you should be able to log in via SSH to the system user and run “su – user” as root to impersonate a system user.
setfacl -x group:GridPane-System-Users /bin
Step 3 – Removing ACL Permissions on /dev
You may also warnings about /dev, there is also an acl placed on /dev
setfacl -x group:GridPane-System-Users /dev
Updating Home Directory Permission
So you can SSH in as a GridPane system user, but you can’t create files in your home directory. This isn’t too bad, but we want to create and modify files in our home directory.
Step 1 – Check System Users Home Directory
Simply change the ownership of the GridPane system users’ home directory as root. Here’s an example of what it will look like by default, the user and group root have ownership.
root@srv01:/home# ls -al total 84 drwxr-xr-x+ 21 root root 4096 Mar 12 17:27 . drwxr-xr-x 23 root root 4096 Mar 20 02:00 .. drwxr-xr-x 4 root root 4096 Mar 17 17:22 wpinfo
Step 2 – Update System Users Ownership
So let’s change the ownership to the GridPane system user and group to wpinfo from root.
root@srv01:/home# chown wpinfo:wpinfo wpinfo
Now you shouldn’t have any issues with writing to your home directory.
Fixing Permissions on /home
There are also improper permissions on /home; it’s owned by root:root
❯ ls -al total 80K drwxr-xr-x+ 20 root root 4096 Feb 26 16:59 . drwxr-xr-x 23 root root 4096 Feb 21 02:00 .. drwxr-xr-x 4 root root 4096 Dec 17 02:07 site
You need to chown the folder as the system user.
chown site:site site
Securing SSH
The changes above lessen security. However, you can look into using rbash

There are other methods available, such as building each user their own chroot environment. But that can become cumbersome.
Updates
- 08-25-2023 – Updated article to include how to enable Visual Studio Code Remote SSH Extension.